Ensure Security & Compliance of Your Citrix Infrastructure
Leverage infrastructure monitoring data for security and compliance reporting
Free TrialMeeting Security & Compliance Requirements
The need to meet regulatory compliance is becoming increasingly essential for enterprises. Encountering security breaches and data leakage lead organizations to bear the brunt of heavy penalties, damage control, and impact on brand value and reputation. Especially for banks, credit unions, healthcare organizations, and government agencies that deal with sensitive client data, it is imperative to keep track of all events and user activity on the network.
Challenges
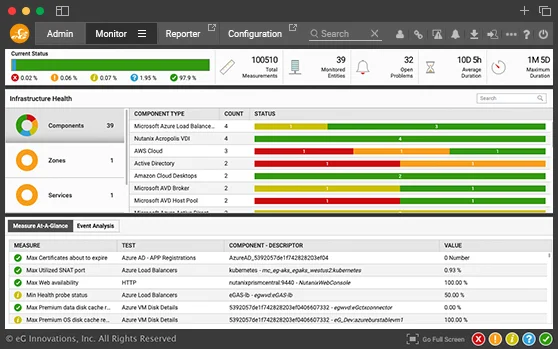
In complex and distributed deployments using technologies such as Citrix, VMware or Cloud Platforms, a wealth of data from infrastructure monitoring intelligently analyzed within our AIOps machine learning analytics can provide early warnings on anomalies and suspicious activity. Application unavailability and performance deviations can be the effect of unauthorized changes in network, server, and database settings.
Network security teams can work with IT operations to scan data collected from monitoring tools, and report on irregularities and inconsistencies in Citrix access, configuration settings, and user activity.
Since we don't control everything between our data center and client locations, events occasionally occur where service availability or application performance issues arise. eG Enterprise helps us pinpoint the nature and origin of the problem right away so we can resume normal operations as quickly as possible.![]()
Features
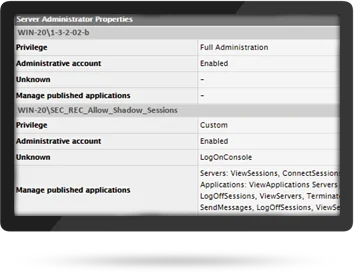
Reporting on Administrative Access Privileges
The individuals that are granted administrative access to a Citrix and/or VMware infrastructure may or may not be the same as those that have AD domain admin permissions. At times, vendors or partners are also given some level of administrative access. From an auditing perspective, it is essential to ascertain exactly who has what type of administrative permissions.
eG Enterprise is a unified monitoring solution that provides visibility into performance and availability of your entire application delivery infrastructure. The built-in reports provide detailed information on which user (administrator or not) has what access privileges in your Citrix and other digital workspace environments.
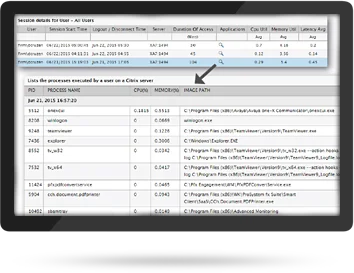
Safeguarding Against Inappropriate User Activity
eG Enterprise lets you monitor when users log into Citrix XenApp or XenDesktop sessions, who logs in, how long do they stay, do they connect at odd hours, are their multiple failed logon attempts. These metrics help you identify suspicious user behavior in your Citrix environment.
Inactive user accounts are concerning because they are often overlooked by administrators. Regularly scheduled ‘inactive users’ report enables security and compliance professionals to adhere to IT regulations.
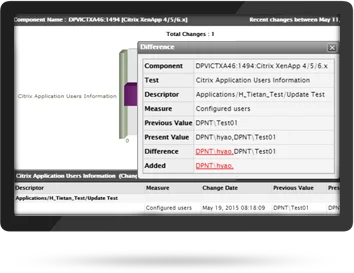
Change Control Verification
Change control documentation is a critical element of security and compliance reviews. Report output of the final system change—such as a new user that is provided with access to an application or resource—may be used as verification that the change control was successfully and completely executed.
eG Enterprise provides detailed reports of configuration changes to your critical infrastructure (applications, servers and virtual machines). Analyze what configuration has changed by comparing it with earlier configuration states.
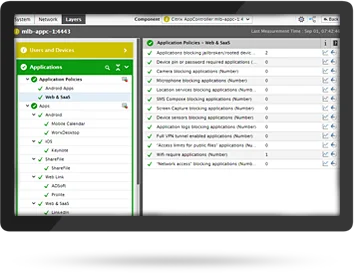
Monitoring Non-Compliant Devices in XenMobile Environment
To maintain confidentiality and data integrity, Citrix admins and security teams need to ensure devices managed by XenMobile are not breaching security policies. eG Enterprise delivers real-time alerts
- On jailbroken and non-compliant devices
- When an employee device leaves a defined perimeter
- When unauthorized apps are installed on devices
- When any suspicious user activity transpires at endpoints
- Whether data wiping has been successful or not, and more