Azure AD - APP Registrations
To delegate identity and access management functions to Azure AD, an application must be registered with an Azure AD tenant. When you register your application with Azure AD,you are creating an identity configuration for your application that allows it to integrate with Azure AD. For this purpose, registration automatically assigns a globally unique ID (application ID) to your app. Besides giving your app an identity, you also need to be mindful of the security requirements of your app during registration. To protect your application and user interactions with it from harm, you should authenticate accesses to the application using secrets and/or certificates. A client secret is the application password, which is auto-generated by Azure during application registration. A more secure authentication option would be certificates. Azure AD certificate-based authentication (CBA) enables customers to allow or require users to authenticate with X.509 certificates against their Azure Active Directory (Azure AD) for applications and browser sign-in. You can create a self-signed certificate for your application, export it to a file, and upload this certificate file when registering your application using the Azure portal.
You can authenticate applications using secrets or certificates or both. However, be it a secret or a certificate, their validity is determined by their expiry date. You can set when the client secret should expire, during application registration. For a certificate on the other hand, the expiry date is set when generating that certificate. An application stays secure only as long as the certificate/secret associated with it is valid/active.
If an application uses an invalid/expired certificate/secret, the security framework of that application will be severely compromised. This may not only impact application functionality, but can also have far-reaching, organization-wide effects (depending upon the permissions granted to that application). If this is to be avoided, administrators will need to be be informed about the expiry of a certificate/secret, and should also be able to quickly identify the application that is tied to expired certificates/secrets. Better still, if an administrator receives a heads up before a certificate/secret expires, it will help him/her take pre-emptive actions and avert potential security disasters. The Azure AD - APP Registrations test helps with all of the above!
This test monitors application registrations on Azure AD, and reports the count and details of applications with invalid or expired secrets/certificates. With this information, administrators can rapidly identify applications with a high security risk quotient, and initiate measures to mitigate those risks. The test also alerts administrators to secrets and certificates that are about to expire, and thus enables administrators take proactive action against impending expiry. Additionally, the test also points administrators to 'unprotected' applications - i.e., applications without certificates or secrets. This way, the test urges administrators to employ either or both of the authentication options that Azure AD provides and secure their critical applications.
Target of the Test: A Microsoft Azure Active Directory
Agent deploying the test: A remote agent
Output of the test: One set of results for the Azure AD tenant being monitored
| Parameters | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Tenant ID |
Specify the Directory ID of the Azure AD tenant to which the target subscription belongs. To know how to determine the Directory ID, refer to Configuring the eG Agent to Monitor Microsoft Azure Active Directory Using Microsoft Graph API |
|
Client ID, Client Password, and Confirm Password |
To connect to Azure AD, the eG agent requires an Access token in the form of an Application ID and the client secret value. If a Microsoft Azure Subscription component is already monitored in your environment, then you would have already created an Application for monitoring purposes. You can provide the Application ID and Client Secret value of that application here. However, if no such application pre-exists, you will have to create one for monitoring Azure AD. To know how to create such an application and determine its Application ID and Client Secret, refer to Configuring the eG Agent to Monitor Microsoft Azure Active Directory Using Microsoft Graph API. Specify the Application ID of the Application in the Client ID text box and the client secret value in the Client Password text box. Confirm the Client Password by retyping it in the Confirm Password text box. |
|
Proxy Host and Proxy Port |
In some environments, all communication with the Azure cloud be routed through a proxy server. In such environments, you should make sure that the eG agent connects to the cloud via the proxy server and collects metrics. To enable metrics collection via a proxy, specify the IP address of the proxy server and the port at which the server listens against the Proxy Host and Proxy Port parameters. By default, these parameters are set to none, indicating that the eG agent is not configured to communicate via a proxy, by default. |
|
Proxy Username, Proxy Password and Confirm Password |
If the proxy server requires authentication, then, specify a valid proxy user name and password in the Proxy Username and Proxy Password parameters, respectively. Then, confirm the password by retyping it in the Confirm Password text box. |
|
Expire Days Limit |
By default, this parameter is set to 90 days. This means that the test, by default, counts the certificates and secrets that will be expiring any time within the next 90 days, and reports those numbers as the values of the Certificates about to expire and Clients secrets about to expire measures, respectively. Also, these measures will raise an alert only if there is at least one certificate/secret that is set to expire within 90 days from the current day. You can change the value of this measure, if you want to be alerted sooner or later to the impending expiry of certificates or secrets. For instance, if you change the value of this parameter to 15, then the test will wait till there are only 15 days for a secret/certificate to expire to alert you to the expiry. On the other hand, if you change the value of the measure to 120 days, then the alert will be sent sooner - i.e., the test will notify you even if a certificate/secret is 4 months away from expiry. |
|
DD Frequency |
Refers to the frequency with which detailed diagnosis measures are to be generated for this test. The default is 1:1. This indicates that, by default, detailed measures will be generated every time this test runs, and also every time the test detects a problem. You can modify this frequency, if you so desire. Also, if you intend to disable the detailed diagnosis capability for this test, you can do so by specifying none against DD frequency. |
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
| Measurement | Description | Measurement Unit | Interpretation |
|---|---|---|---|
|
App registrations count |
Indicates the number of applications that are registered with Azure AD. |
Number |
|
|
App registrations having valid certificate/client-secrets |
Indicates the number of app registrations with valid certificates/secrets. |
Number |
Use the detailed diagnosis of this measure to know which app registrations have valid certificates/secrets. The details of these valid certificates/secrets are also provided as part of detailed metrics. |
|
App registrations having no certificate/client-secrets |
Indicates the number of app registrations without any certificates/client-secrets. |
Number |
Use the detailed diagnosis of this measure to identify those applications that are not authenticated by any secrets/certificates. The permissions these applications have are also displayed as part of detailed metrics. From the scope of these permissions, you can infer if such applications may be a flight risk to the security ofthe Azure cloud organization and its resources. You may want to consider authenticating accesses to such applications using certificates/secrets, so that the security risks are eliminated. |
|
App registrations having expired certificate/client-secrets |
Indicates the number of app registrations having certificates/client-secrets that have expired. |
Number |
Using the detailed diagnosis of this measure, you can identify those app registrations that are having expired certificates/secrets. You may want to renew the certificates or change the expiry date of the secrets to ensure that the applications stay protected. |
|
Certificates count |
Indicates the total number of certificates uploaded to Azure AD. |
Number |
|
|
Valid certificates count |
Indicates the number of certificates on Azure AD that are currently valid. |
Number |
|
|
Expired certificates count |
Indicates the number of app registration certificates that have expired. |
Number |
Use the detailed diagnosis of this measure to know which certificates have expired, when, which apps use them, and what permissions the apps have. This will tell you whether the applications left unprotected by expired certificates will expose your Azure organization to malicious attacks. |
|
Certificates about to expire |
Indicates the number of certificates that will be expiring within the duration specified against the Expiry Days Limit parameter.. |
Number |
Ideally, the value of this measure should be 0. A non-zero value is a cause for concern Use the detailed diagnosis of this measure to know which certificates are about to expire, when, which apps use them, and what permissions the apps have. With the help of this information, you can initiate measures to avert security disasters that may occur in the event that the certificates do expire. |
|
Client secrets count |
Indicates the total number of client secrets assigned to app registrations on Azure AD, |
Number |
|
|
Valid client secrets count |
Indicates the number of client secrets that are currently valid, |
Number |
|
|
Expired client secrets count |
Indicates the number of app registration client secrets that have expired. |
Number |
Use the detailed diagnosis of this measure to know which client secrets have expired, when, which apps use them, and what permissions the apps have. This will tell you whether the applications left unprotected by expired clien certificates will expose your Azure organization to malicious attacks. |
|
Client secrets about to expire |
Indicates the number of client secrets that will be expiring within the duration specified against the Expiry Days Limit parameter. |
Number |
Ideally, the value of this measure should be 0. A non-zero value is a cause for concern. Use the detailed diagnosis of this measure to know which client secrets are about to expire, when, which apps use them, and what permissions the apps have. With the help of this information, you can initiate measures to avert security disasters that may occur in the event that the secrets do expire. |
|
App registrations having both certificate & client-secrets |
Indicates the number of app registrations authenticated using both certificates and client secrets. |
Number |
|
|
New app registrations created recently |
Indicates the number of apps that were registered during the last measurement period. |
Number |
The detailed diagnosis of this measure reveals the names of the recently registered apps, their IDs, when they were created, and what permissions were granted to them. |
|
New certificates created recently |
Indicates the number of certificates that were created during the last measurement period. |
Number |
The detailed diagnosis of this measure reveals the ID and expiry date of the certificates that were created recently, and which applications are currently using these certificates. |
|
New client secrets created recently |
Indicates the number of client secrets that were created during the last measurement period. |
Number |
The detailed diagnosis of this measure reveals name the and expiry date of the client secrets that were created recently, and which applications are currently using these secrets. |
Use the detailed diagnosis of the App registrations having valid certificate/client-secrets measure to know which app registrations have valid certificates/secrets. The details of these valid certificates/secrets are also provided as part of detailed metrics.
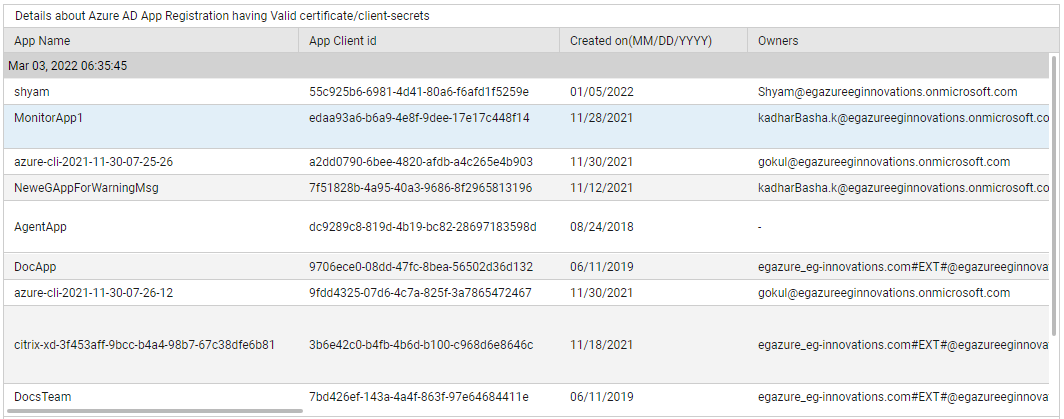
Figure 1 : The detailed diagnosis of the App registrations having valid certificate/client-secrets measure
Use the detailed diagnosis of the App registrations having no certificate/client-secrets measure to identify those applications that are not authenticated by any secrets/certificates. The permissions these applications have are also displayed as part of detailed metrics.
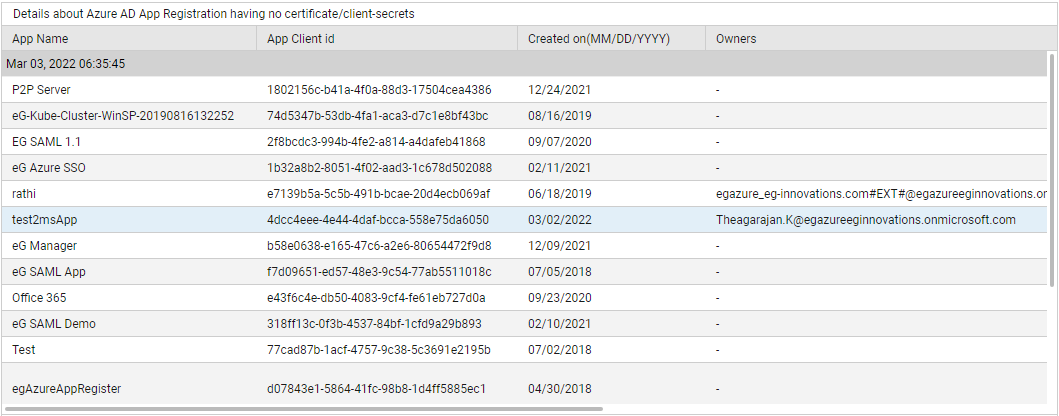
Figure 2 : The detailed diagnosis of the App registrations having no certificate/client-secrets measure
Using the detailed diagnosis of the App registrations having expired certificate/client-secrets measure, you can identify those app registrations that are having expired certificates/secrets.
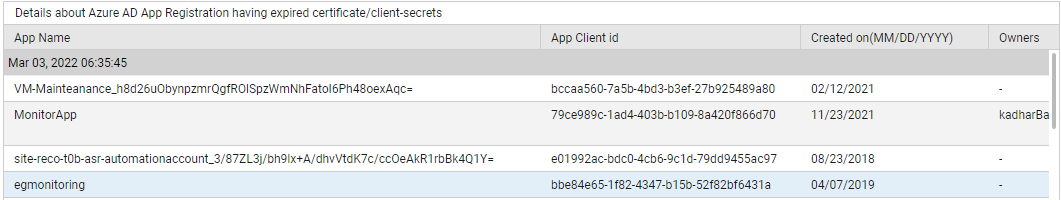
Figure 3 : The detailed diagnosis of the App registrations having expired certificate/client-secrets measure
Use the detailed diagnosis of the Expired certificates count measure to know which certificates have expired, when, which apps use them, and what permissions the apps have.
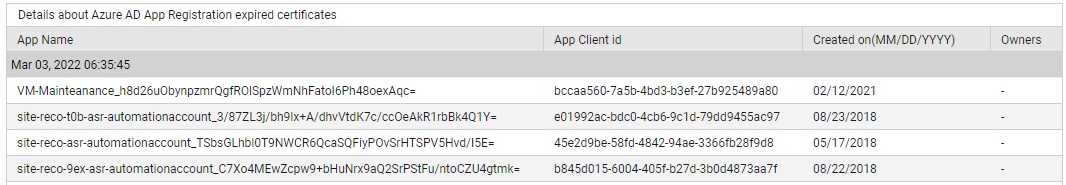
Figure 4 : The detailed diagnosis of the Expired certificates count measure
Use the detailed diagnosis of the Expired client secrets count measure to know which client secrets have expired, when, which apps use them, and what permissions the apps have.
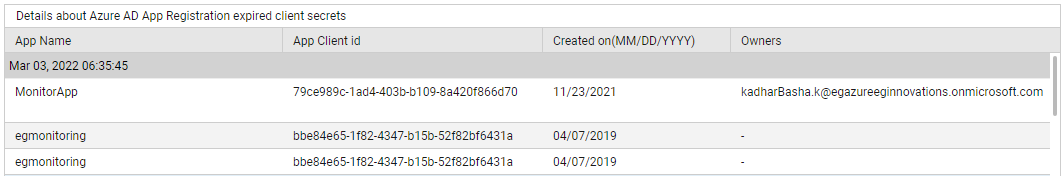
Figure 5 : The detailed diagnosis of the Expired client secrets count measure
Use the detailed diagnosis of the Client secrets about to expire measure to know which client secrets are about to expire, when, which apps use them, and what permissions the apps have.
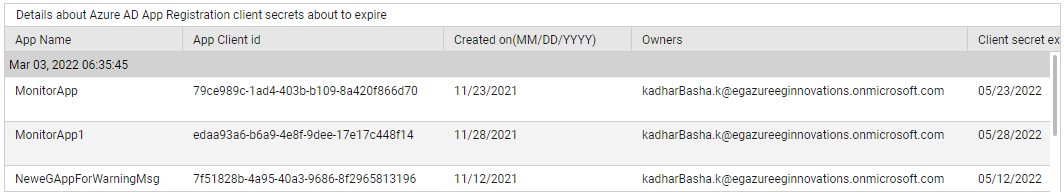
Figure 6 : The detailed diagnosis of the Client secrets about to expire measure
