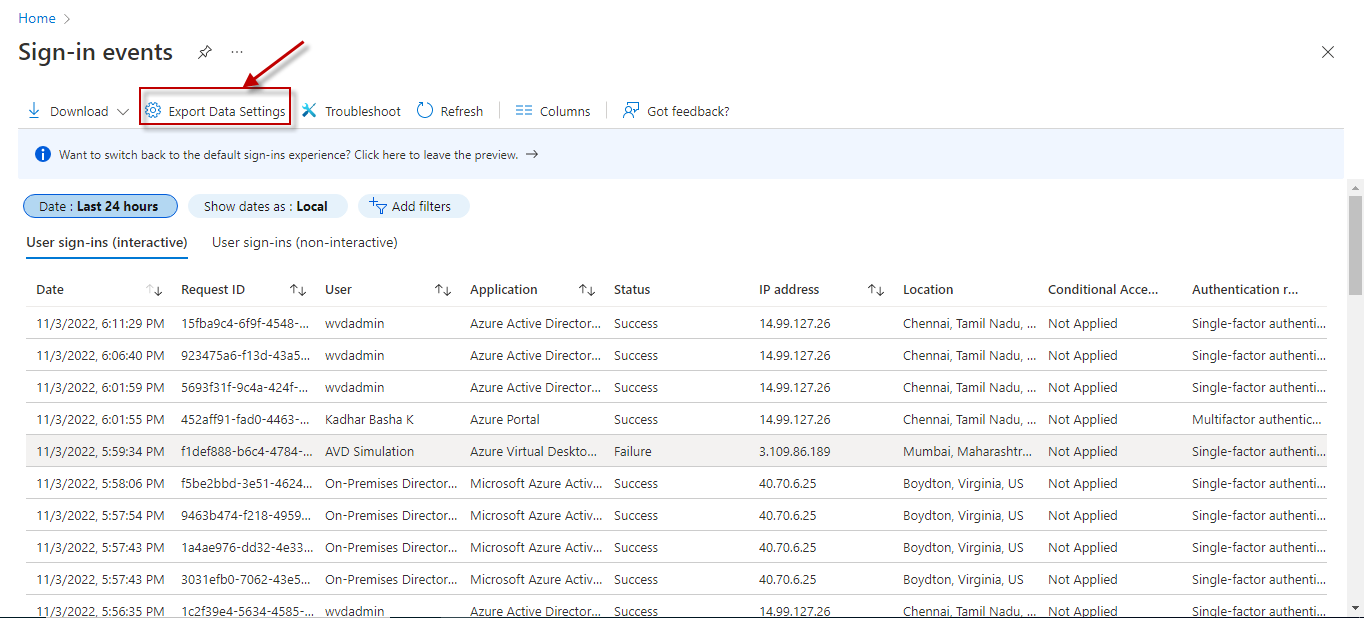
Azure Interactive Sign-ins Test
The Sign-in logs provided by the Azure Active Directory (AD) portal is a treasure-chest of information about user sign-ins to the Azure organization and how signed-in users use the organization's resources.
One of the four types of sign-in logs offered by Azure AD is the Interactive Sign-ins log. Interactive user sign-ins are sign-ins where a user provides an authentication factor to Azure AD or interacts directly with Azure AD or a helper app, such as the Microsoft Authenticator app. The factors users provide include passwords, responses to MFA challenges, biometric factors, or QR codes that a user provides to Azure AD or to a helper app.
In the interest of secuity, it would do an administrator a lot of good to know what type of authentication was used for the interactive sign-ins - legacy authentication or modern authentication. This analysis will point them to authentication methods that are less secure, so they are prompted to disable them for a tenant, if required.
Also, a sign-in failure always leaves a bad taste; if it happens too frequently, it can damage the total Azure sign-in experience of users. To assure users of a superlative experience, an administrator should be able to spot sign-in failures rapidly, find out the reasons for the same, and fix them.
Moreover, its not always about whether a sign-in succeeds/fails. An administrator should also pay attention to risky sign-ins and deviant sign-in patterns. For instance, if an unusually large number of sign-ins are coming from a specific user/IP address/location/protocol or for a specific application/service principal/resource, it could imply that someone is trying to hack into your Azure organization and take control of its resources. Administrators should be able to spot such patterns quickly and scrutinize them, so as to avert any potential security disasters.
With the help of the Azure Interactive Sign-ins test, an administrator can achieve all of the above!
This test monitors Azure interactive sign-in logs for failed sign-ins and reports their count and details. With the help of these details, administrators can effectively troubleshoot the failures. The test also promptly captures and reports 'risky sign-ins', so that dubious sign-in attempts can be investigated and prevented. Additionally, the test reveals whether any sign-ins were made using unsecure legacy authentication protocols. Since such authentication protocols are a security threat, administrators may want to disable them. The test also helps administrators closely scrutinize the sign-ins to isolate abnormal patterns, such as the following:
-
Are there an unusually high number of sign-ins coming from specific IP addresses/locations/users/protocols?
-
Are any applications/service principals/resources making a suspicious number of sign-in attempts?
-
Are sign-in attempts from specific users/IP addresses/locations failing often?
-
Are specific applications/service principals/resources seeing more sign-in failures than others?
This way, the test sheds light on sign-in attempts that are 'suspect', so their authenticity can be verified, and any potential security risks pre-empted.
Target of the Test: A Microsoft Azure Active Directory
Agent deploying the test: A remote agent
Output of the test: One set of results for the Azure Active Directory tenant being monitored
| Parameters | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Tenant ID |
Specify the Directory ID of the Azure AD tenant to which the target subscription belongs. To know how to determine the Directory ID, refer to Configuring the eG Agent to Monitor Microsoft Azure Active Directory |
|
Client ID, Client Password, and Confirm Password |
The eG agent communicates with the target Microsoft Azure Subscription using Java API calls. To collect the required metrics, the eG agent requires an Access token in the form of an Application ID and the client secret value. To know how to determine the Application ID and the key, refer to Configuring the eG Agent to Monitor Microsoft Azure Active Directory. Specify the Application ID of the created Application in the Client ID text box and the client secret value in the Client Password text box. Confirm the Client Password by retyping it in the Confirm Password text box. |
|
Proxy Host and Proxy Port |
In some environments, all communication with the Azure cloud be routed through a proxy server. In such environments, you should make sure that the eG agent connects to the cloud via the proxy server and collects metrics. To enable metrics collection via a proxy, specify the IP address of the proxy server and the port at which the server listens against the Proxy Host and Proxy Port parameters. By default, these parameters are set to none, indicating that the eG agent is not configured to communicate via a proxy, by default. |
|
Proxy Username, Proxy Password and Confirm Password |
If the proxy server requires authentication, then, specify a valid proxy user name and password in the Proxy Username and Proxy Password parameters, respectively. Then, confirm the password by retyping it in the Confirm Password text box. |
|
Log Analytics Workspace Name |
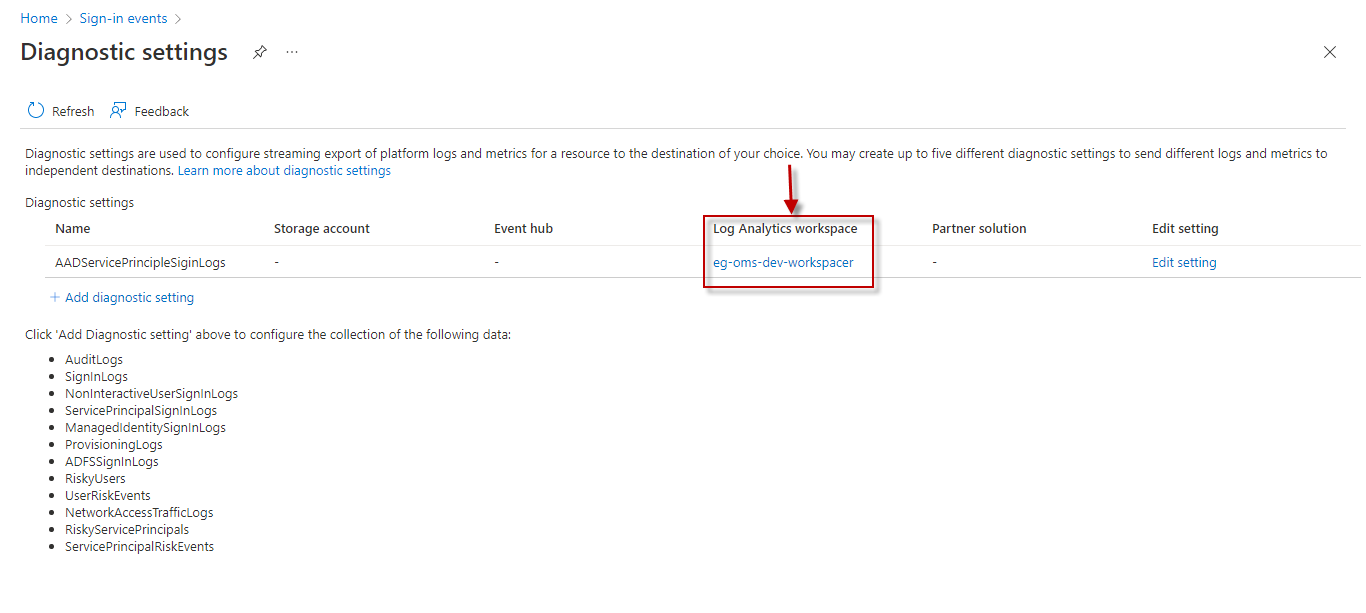
Typically, Interactive Sign-in logs are sent to a Log Analytics Workspace. By default, the Log Analytics Workspace Name parameter is set to All. This indicates that the test reads sign-in data from all Log Analytics Workspaces configured for the target tenant, by default. However, if you want the test to monitor only specific Log Analytics Workspaces, then provide the names of these workspaces here as a comma-separated list. To determine the names of such workspaces, do the following:
However, If the Log Analytics workspace column in Figure 3 is blank for all the existing diagnostic settings, it is a clear indication that the sign-in logs are not yet configured to be sent to any Log Analytics Workspace. In this case therefore, you should create a new diagnostic setting, where a Log Analytics Workspace is configured as the destination for the Sign-in logs. To achieve this, follow the procedure detailed in Configuring the Sign-in Logs to be Sent to a Log Analytics Workspace. |
|
Successful Signin DD |
By default, this flag is set to No. This means that, by default, this test will not report detailed diagnostics for the 'Success' metrics (eg., Successful sign-ins, Success IP addresses etc.). This is because, in a typical Azure cloud organization, there may be numerous successful sign-in attempts. A well-tuned, well-sized eG database is required for storing these detailed metrics. Without it,over a period of time, the detailed statistics of 'Successful' sign-in attempts may end up choking the eG database. To avoid it, this parameter is set to No by default. Set this flag to Yes only if your eG database has sufficient space to store detailed diagnostics for the 'Success' metrics. |
|
No of Attempts |
By default, this flag is set to 5. This means that, by default, the test will count a sign-in attempt from a specific user / IP address / location / protocol or for a specific application / service principal / resource as a success/failure, only if 5 or more consecutive sign-in attempts from/for that entity succeed/fail (as the case may be). For instance, if 5 or more sign-in attempts from a specific IP address fail, then the test will count that as one failure - i.e., the Failure IP addresses measure will report the value 1. Similarly, if 5 or more sign-in attempts from a specific IP address succeed, then the test will count that as a single sign-in success - i.e., the Success IP addresses measure will report the value 1. Needless to say, by default, the values of these measures will also be incremented only with every 5 or more consecutive sign-in successes/failures. This is done so that administrators are alerted only to those sign-in attempts that are 'suspect' - for example, repeated sign-in failures from the same IP address. You can change the value of this measure based on what is normal sign-in activity and what is not in your environment. This parameter applies to the following measures reported by the test:
|
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
| Measurement | Description | Measurement Unit | Interpretation |
|---|---|---|---|
|
Total interactive sign-ins |
Indicates the total number of interactive sign-ins attempted. |
Number |
|
|
Success sign-ins |
Indicates the number of sign-in attempts that were successful. |
Number |
Use the detailed diagnosis of this measure to know which sign-in attempts succeeded. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Failed sign-ins |
Indicates the number of sign-in attempts that failed. |
Number |
Ideally, the value of this measure should be 0. Use the detailed diagnosis of this measure to know which sign-in attempts failed. |
|
Risky sign-ins |
Indicates the number of risky interactive sign-in attempts. |
Number |
In Azure AD Identity Protection, risk detections include any identified suspicious actions related to user accounts in Azure AD. Ideally, the value of this measure should be 0. If a non-zero value is reported, then use the detailed diagnosis of this measure to know the risky sign-in attempts. |
|
Successful IP addresses |
Indicates the number of IP addresses from which successful sign-in attempts were made. |
Number |
Use the detailed diagnosis of this measure to know from which IP addresses successful sign-in attempts were made. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Successful locations |
Indicates the number of locations from which successful sign-in attempts were made. |
Number |
Use the detailed diagnosis of this measure to know from which locations successful sign-in attempts were made. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Successful applications |
Indicates the number of applications that successfully used managed identities to sign into Azure. |
Number |
Use the detailed diagnosis of this measure to know which applications signed into Azure successfully. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Successful service principals |
Indicates the number of service principals that successfully used managed identities to sign into Azure. |
Number |
Use the detailed diagnosis of this measure to know which service principals signed into Azure successfully. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Successful resources |
Indicates the number of services that were used in successful sign-ins. |
Number |
Use the detailed diagnosis of this measure to know which services were used in successful sign-ins. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Successful users |
Indicates the number of users who successfully signed in. |
Number |
Use the detailed diagnosis of this measure to know which users' sign-in attempts succeeded. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Successful authentication protocols |
Indicates the number of authentication protocols that were used in successful sign-ins. |
Number |
Use the detailed diagnosis of this measure to know which protocols were used in successful sign-ins. Note that this measure will report detailed diagnostics only if the Successful Signin DD parameter of this test is set to Yes. |
|
Failed sign-ins percentage |
Indicates the percentage of sign-in attempts that failed. |
Number |
Ideally, the value of this measure should be low. Use the detailed diagnosis of this measure to know which sign-in attempts failed. |
|
Failure IP addresses |
Indicates the number of IP addresses from which sign-in attempts failed. |
Number |
Use the detailed diagnosis of this measure to know from which IP addresses the maximum number of failed sign-in attempts were made. You may want to investigate these attempts to figure out if they were geniuine attempts or malicious attacks. |
|
Failure locations |
Indicates the number of locations from which sign-in attempts failed. |
Number |
Use the detailed diagnosis of this measure to know from which locations the maximum number of failed sign-in attempts were made. You may want to investigate these attempts to figure out if they were geniuine attempts or malicious attacks. |
|
Failure applications |
Indicates the number of applications that were unable to sign-into Azure. |
Number |
Use the detailed diagnosis of this measure to know which applications failed to sign into Azure the maximum number of times. You may want to investigate these attempts to figure out if they were geniuine attempts or malicious attacks. |
|
Failure service principals |
Indicates the number of service principals that could not sign into Azure. |
Number |
Use the detailed diagnosis of this measure to know which service principals failed to sign into Azure the maximum number of times. You may want to investigate these attempts to figure out if they were geniuine attempts or malicious attacks. |
|
Failure resources |
Indicates the number of services that were used in failed sign-ins. |
Number |
Use the detailed diagnosis of this measure to know which services were used in the maximum number of failed sign-ins. You may want to investigate these attempts to figure out if they were geniuine attempts or malicious attacks. |
|
Failure users |
Indicates the number of users whose sign-in attempts failed. |
Number |
Use the detailed diagnosis of this measure to know which users experienced the maximum number of failed sign-ins. You may want to investigate these attempts to figure out if they were geniuine attempts or malicious attacks. |
|
Failure authentication protocols |
Indicates the number of authentication protocols that were used in failed sign-in attempted. |
Number |
Use the detailed diagnosis of this measure to know which were used in the maximum number of failed sign-ins. You may want to investigate these attempts to figure out if they were geniuine attempts or malicious attacks. |
|
Single-factor authentications |
Indicates the number of sign-ins made using the single-factor authentication method. |
Number |
Use the detailed diagnosis of this measure to view the sign-ins made using single-factor authentication. |
|
Multi-factor authentications |
Indicates the number of sign-ins made using the multi-factor authentication method. |
Number |
Use the detailed diagnosis of this measure to view the sign-ins made using multi-factor authentication. |
|
Modern client authentications |
Indicates the number of sign-ins that used modern client authentication techniques. |
Number |
Modern authentication is a method of identity management that offers more secure user authentication and authorization. Modern authentication is an umbrella term for a combination of authentication and authorization methods between a client (for example, your laptop or your phone) and a server, as well as some security measures that rely on access policies that you may already be familiar with. Use the detailed diagnosis of this measure to view the sign-ins made using modern client authentication. |
|
Legacy client authentications |
Indicates the number of sign-ins that used legacy client authentication techniques. |
Number |
Legacy authentication refers to basic authentication, which was once a widely used industry-standard method for passing user name and password information through a client to an identity provider. Use the detailed diagnosis of this measure to view the sign-ins made using legacy client authentication. |
|
Not applied conditional accesses |
Indicates the number of sign-ins during which no conditional access policy applied to the user and application. |
Number |
Conditional Access policies at their simplest are if-then statements, if a user wants to access a resource, then they must complete an action. Example: A payroll manager wants to access the payroll application and is required to do multi-factor authentication to access it. |
|
Successful conditional accesses |
Indicates the number of sign-ins during which one or more conditional access policies applied to the user and application. |
Number |
|
|
Failed conditional accesses |
Indicates the number of sign-ins that satisfied the user and application condition of at least one Conditional Access policy and grant controls are either not satisfied or set to block access. |
Number |
Use the detailed diagnosis of this measure to know which conditional access policies failed. |
Use the detailed diagnosis of the Failed sign-ins and Failed sign-ins percentage measure to know which sign-in attempts failed.
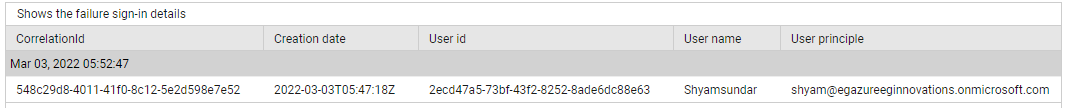
Figure 4 : The detailed diagnosis of the Failed sign-ins measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Risky sign-ins measure to know the risky sign-in attempts.
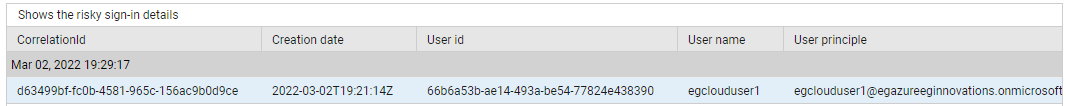
Figure 5 : The detailed diagnosis of the Risky sign-ins measure
Use the detailed diagnosis of the Single-factor authentications measure to view the sign-ins made using single-factor authentication.
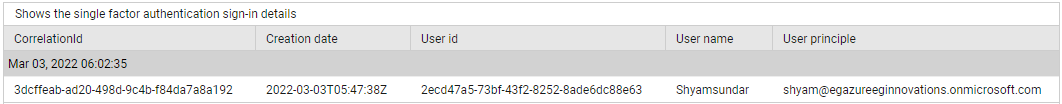
Figure 6 : The detailed diagnosis of the Single-factor authentications measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Multi-factor authentications measure to view the sign-ins made using multi-factor authentication.
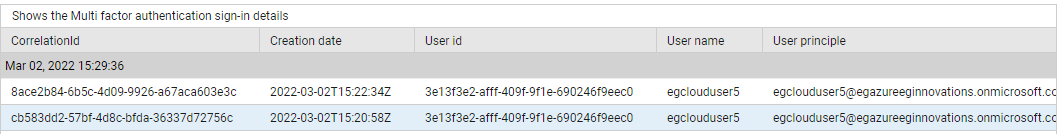
Figure 7 : The detailed diagnosis of the Multi-factor authentications measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Modern client authentications measure to view the sign-ins made using modern client authentication.
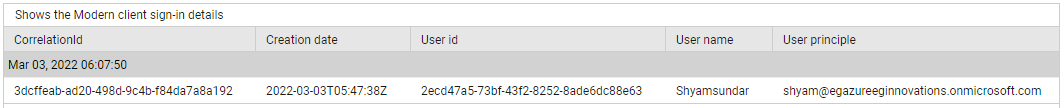
Figure 8 : The detailed diagnosis of the Modern client authentications measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Failed conditional accesses measure to know which conditional access policies failed.
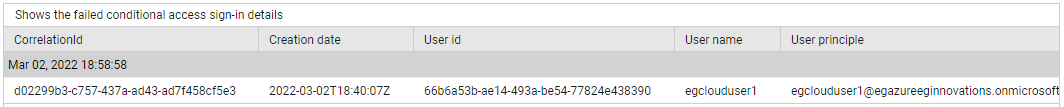
Figure 9 : The detailed diagnosis of the Failed conditional accesses measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Successful IP addresses measure to know from which IP addresses successful sign-in attempts were made.
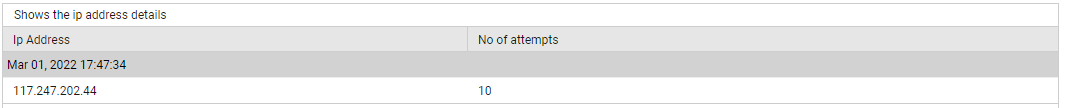
Figure 10 : The detailed diagnosis of the Successful IP addresses measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Successful locations measure to know from which locations successful sign-in attempts were made.
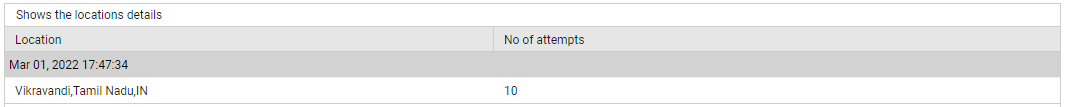
Figure 11 : The detailed diagnosis of the Successful locations measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Successful applications measure to know which applications signed into Azure successfully.
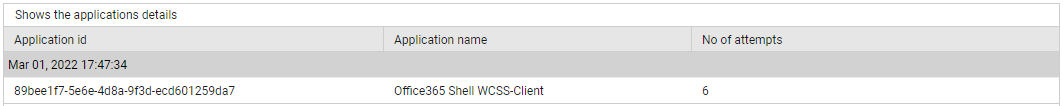
Figure 12 : The detailed diagnosis of the Successful applications measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Successful resources measure to know which services were used in successful sign-ins.
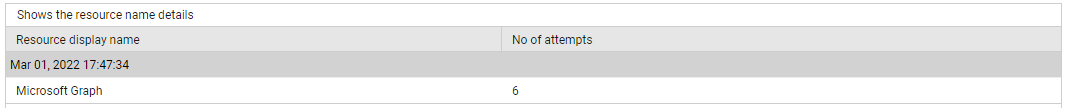
Figure 13 : The detailed diagnosis of the Successful resources measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Successful users measure to know which users' sign-in attempts succeeded.
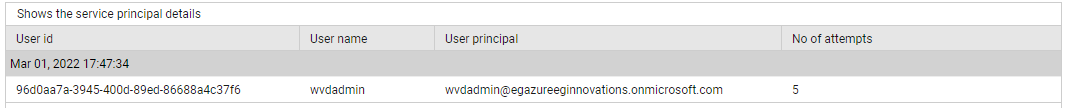
Figure 14 : The detailed diagnosis of the Successful users measure of the Azure Interactive Sign-ins test
Use the detailed diagnosis of the Successful authentication protocols measure to know which protocols were used in successful sign-ins.
Figure 15 : The detailed diagnosis of the Successful authentication protocols measure of the Azure Interactive Sign-ins test