How does eG Enterprise Monitor a Generic SMI-S Compliant Storage Device?
Storage Raid is an “agentless” monitoring model, which requires that an eG agent to be deployed on a remote host in the environment. Once configured, this eG agent will poll the SMI-S Provider of the target storage system at set intervals and collect the required performance metrics. To know where to install this eG agent and how to configure the agent to interact with the SMI-S Provider, follow the guidelines discussed below:
-
Know how the SMI-S Provider has been implemented in the storage system to be monitored
SMI-S defines CIM management profiles for storage systems. A profile describes the behavioral aspects of an autonomous, self-contained management domain. SMI-S includes profiles for Arrays, Switches, Storage Virtualizers, Volume Management and many other domains. In DMTF parlance, a provider is an implementation for a specific profile. Using the "provider" (the actual software library), a management application (SMI-S Client) doesn't require knowledge of the specific architecture or infrastructure requirements of the particular storage platform.
SMI-S providers can be implemented either as proxies to the devices or as embedded software within the actual storage platform.
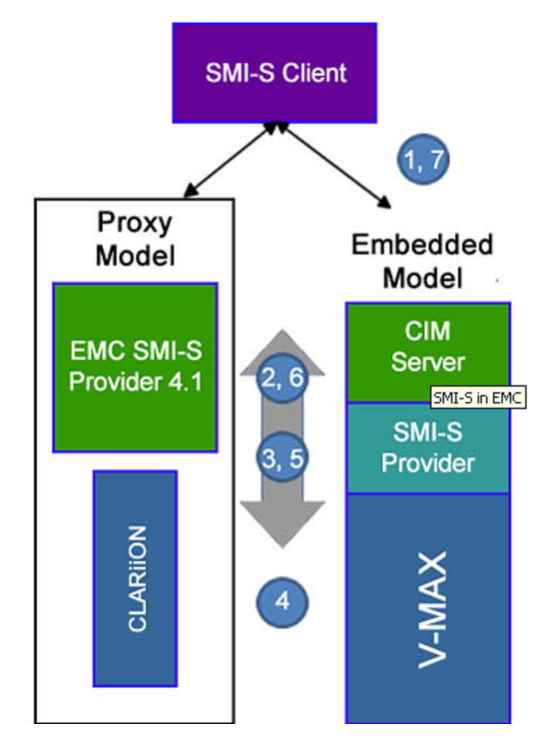
Figure 2 : Implementation options for SMI-S Providers
Most legacy storage platforms have implemented their SMI-S providers as proxies. The proxies are software libraries external from the storage platforms that accept SMI-S queries and commands, and translate them into vendor specific commands which they send to the storage platforms.
As the name implies, the embedded SMI-S providers are included on the storage platforms and do not require the installation or maintenance of a separate software package to provide an SMI-S interface to the storage platform. The trend for the newer platforms is to embed the SMI-S providers within the storage system as evidenced by the latest IBM DS8000 platforms and the EMC V-Max platforms.
Before deploying the eG agent, know how the SMI-S provider of the target storage system has been implemented – as a proxy? or as an embedded software?.
-
Choose the host for eG agent deployment based on how the SMI-S Provider has been implemented in the storage system.
If the SMI-S provider has been implemented as a proxy, then the eG agent should be deployed on the same host as the SMI-S provider. On the other hand, if the provider has been embedded in the storage platform, the eG agent can be deployed on any remote Windows host in the environment. However, in the case of the latter, make sure that the Windows host is able to connect to the SMI-S provider and pull out metrics related to the storage system.
-
Ensure that the SMI-S Provider is enabled and started on the storage system.
-
Manage the target storage system using the eG administrative interface
You need to provide a Host IP when managing the storage system using the eG admin interface. This Host IP specification varies according to the SMI-S Provider implementation. If the provider is an embedded software, then specify the IP address of the storage system as the Host IP. If the provider is a proxy, then enter the IP address of the host on which the SMI-S Provider software has been installed as the Host IP.
-
Configure tests for the storage raid that has been managed
When configuring tests, you need to configure the eG agent with the following:
- Whether the SMI-S Provider has been implemented as a proxy or as an embedded software.
-
The serial number of the storage device to be monitored, in case the SMI-S Provider has been implemented as a proxy
This is because, the proxy implementation of the provider can manage multiple devices at the same time. The serial number is the unique identifier that will enable the eG agent to collect metrics from the right storage device.
-
Credentials of an SMI-S provider CIM user who has the right to access the storage device, execute API commands on it and pull out the desired metrics
The exact role that is to be assigned to such a user will differ from one device to another – for instance, when monitoring 3PAR, you will have to provide the credentials of a user who has been assigned the Monitor role.
- The namespace that uniquely identifies the profiles specific to the SMI-S provider in use.