Architecture of AD FS
Active Directory Federation Services consists of four major components:
-
Active Directory: This is where all the identity information is stored to be used by ADFS.
-
Federation server: Contains the tools needed to manage federated trusts between business partners, and hosts the “Federation Service” role service of ADFS. It routes requests that come in from external users and also hosts a security token service that issues tokens for claims based on verification of credentials from AD.
-
Federation server proxy: Hosts the Federation Service Proxy role service of ADFS. External clients connect to this proxy server when requesting the security token. It’s deployed in your organization’s perimeter network (DMZ or extranet). This is done because the federation server is not exposed directly to the internet as it is heavily dependent on the AD—doing so would be a major security risk. So the proxy server forwards the requests from the outside world to the federation server.
-
ADFS web server: Hosts either the claims-aware or the Windows token-based ADFS Web Agent role service. This web agent manages security tokens and authentication cookies that are sent to the web server for authenticating external users.
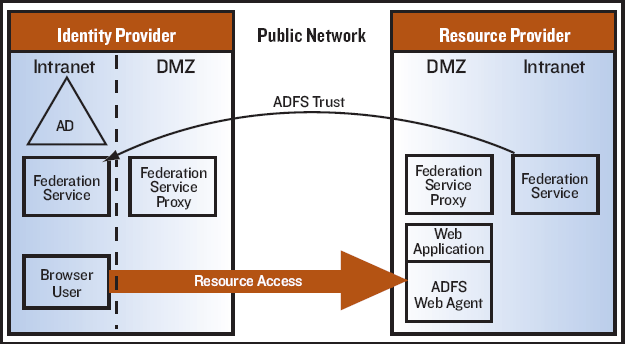
Figure 1 : Architecture of AD FS
From the above discussion, it is clear that one of the key components of AD FS is the Federation Server. Let take a closer look at it.