Sessions - AVD Test
This test reports performance statistics related to user sessions to the chosen Session Host / Azure Virtual Desktop.
Target of the test : An Azure Virtual Desktop
Agent deploying the test : An internal agent.
Outputs of the test : One set of results for the chosen Session Host / Azure Virtual Desktop
| Parameters | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Port |
The default port is NULL. |
|
Report Using Manager Time |
By default, this flag is set to Yes. This indicates that the user login time displayed in the detailed diagnosis page for this test will be based on the eG manager's time zone by default. Set this flag to No if you want the login times displayed in the detailed diagnosis page for this test to be based on the target AVD's local time. |
|
Report By Domain Name |
By default, this flag is set to Yes. This implies that by default, the detailed diagnosis of this test will display the domainname\username of each user who logged into the chosen Session Host / Azure Virtual Desktop. This way, administrators will be able to quickly determine which user logged in from which domain. If you want the detailed diagnosis to display the username alone, then set this flag to No. |
|
Ignore Down Session IDs |
By default, this parameter is set to 65536,65537,65538. If any of these ports go down, then by default, this test will not count any of the sessions that failed when attempting to connect to that port as a Down session. You can override this default setting by adding more ports or by removing one/more existing ports. |
|
Automated Action Enabled |
In multi-user virtual environments like Azure Virtual Desktop environments, server resources are shared by all user sessions on that server. In such environments therefore, it is important to ensure that users engaged in business-critical operations have the resources they need. A resource shortage can not only impair user productivity, but can also bring crucial business processes to a halt, and can severely degrade overall user experience with the application delivery service. To avoid such an outcome, administrators need to rapidly identify and intelligently manage those types of user sessions that consume resources unnecessarily - i.e., user sessions that are 'unproductive resource consumers'. This way, administrators can make sure that adequate resources are always available for carrying out important business tasks. Idle sessions and disconnected sessions on a server are often considered to be a waste of valuable resources. If administrators are empowered to quickly identify these sessions and automatically eliminate them or limit their resource usage, they can:
To enable administrators to achieve all of the above, eG Enterprise offers 'Automation Actions'. These actions are governed by the 'Automation Action Enabled' flag. This flag, if enabled, automatically initiates user-configured actions on idle and disconnected sessions, so that they do not consume more resources than they should. Such an action can restrict the amount of resources used by these sessions, change the priority level of processes running in these sessions, and completely log off the sessions. Note: The 'Automation Action Enabled' parameters, once configured, will apply only to the chosen component. These settings will not be applied to other components even if the Apply to other components button is clicked in the Specific Test Configuration page. |
|
Processes to Ignore |
This parameter appears only if the Automated Action Enabled flag is set to Yes. Administrators may want to allow a few critical processes - e.g., key operating system-level processes - unrestricted access to resources. This is because, applying resource usage limits to such critical processes might sometimes have unintended effects, including slow system responsiveness. To prevent such anomalies, administrators can use the Processes to ignore parameter. Specify a comma-separated list of processes that should be excluded from automatic resource usage optimization. For example, your specification can be: Sophos UI,SearchApp. |
|
Idle Sessions Action Enabled |
This parameter appears only if the Automated Action Enabled flag is set to Yes. Idle sessions on the target server are serious resource-drainers! Such sessions do not execute any operations, but consume resources significantly, thereby depriving critical sessions of the resources. To prevent this, administrators need to quickly capture idle sessions, and initiate measures to either terminate such sessions or cap their resource usage. This can be easily achieved using the Idle Sessions Action Enabled flag. This flag, if enabled, ensures that a user-configured action is automatically triggered on sessions that are identified as 'idle'. |
|
Idle Session Time Limit in Minutes |
This parameter appears only if the Automated Action Enabled flag is set to Yes and the Idle Sessions Action Enabled flag is set to Yes. Specify the duration (in minutes) of inactivity beyond which a session is considered to be “idle” by this test. By default, this parameter is set to 30 (minutes). This implies that by default, the test counts all sessions that have been inactive for over 30 minutes as idle sessions. Automated actions will be performed on such sessions only. |
|
Idle Session Action |
This parameter appears only if the Automated Action Enabled and Idle Sessions Action Enabled flags are set to Yes. Here, you can choose either one or both actions that this test should automatically perform on an idle session. The options are as follows:
Note that the chosen action will not be triggered for the processes configured against the Processes to Ignore parameter. |
|
Trim-to Memory Limit of the Process in MB |
This parameter appears only if:
In this text box, specify the maximum amount of memory that any process running in an idle session can consume. By default, the value of this parameter is set to 10 MB. This implies that, by default, a process running in an idle session will not be allowed to consume more than 10 MB of memory, regardless of the memory capacity of the target server. This prevents wastage of memory resources by idle sessions, and also ensures that sessions running critical business applications do not run out of memory. |
|
Disconnected Sessions Action Enabled |
This parameter appears only if the Automated Action Enabled flag is set to Yes. When a user abruptly disconnects his/her session, the applications started by the user will keep running on the target Session Host / Azure Virtual Desktop, consuming resources. This can lead to unnecessary resource consumption on the server. Hence, it is important to identify disconnected sessions and optimize their resource usage before they cause a serious resource contention on the server. This can be easily achieved using the Disconnected Sessions Action Enabled flag. This flag, if enabled, ensures that user-configured actions are automatically performed on sessions that are identified as disconnected sessions. |
|
Disconnected Session Time Limit in Minutes |
This parameter appears only if the Automated Action Enabled and Disconnected Sessions Action Enabled flags are set to Yes. This parameter enables administrators to specify how long a session should be disconnected from the target server for it to considered as a 'disconnected' session by this test. By default, this is set to 10 minutes. This means that any session that has remained disconnected from the server for 10 minutes and over, will be counted as a 'disconnected' session for the purpose of performing automated actions. |
|
Disconnected Session Action |
This parameter appears only if the Automated Action Enabled and Disconnected Sessions Action Enabled flags are set to Yes.. Here, you can choose the action that this test should automatically perform on a disconnected session. The recommended actions are:
Note that the chosen action will not be triggered for the processes configured against the Processes to Ignore parameter. |
|
DD Frequency |
Refers to the frequency with which detailed diagnosis measures are to be generated for this test. The default is 1:1. This indicates that, by default, detailed measures will be generated every time this test runs, and also every time the test detects a problem. You can modify this frequency, if you so desire. Also, if you intend to disable the detailed diagnosis capability for this test, you can do so by specifying none against DD Frequency. |
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
| Measurement | Description | Measurement Unit | Interpretation | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Established sessions |
Indicates the number of active user sessions currently on the AVD. |
Number |
This measure gives an idea of the server workload in terms of active sessions. Tracking the number of active sessions with time, an administrator can obtain information that can help him/her plan the capacity of their AVD environment. The detailed diagnosis capability, if enabled, lists the active, inactive sessions on the AVD |
||||||||||||||
|
Idle sessions |
Indicates the number of sessions that are initialized and are currently ready to accept connections. |
Number |
For performance reasons, the number of idle sessions should be less than ten. |
||||||||||||||
|
Connected sessions |
Indicates the current number of sessions that are connected, but no user has logged on to the AVD. |
Number |
A consistent increase in the value of this measure could indicate that users are having trouble logging in. Further investigation may hence be required. |
||||||||||||||
|
Connecting sessions |
Indicates the number of sessions that are in the process of connecting. |
Number |
A very high value for this measure indicates a problem with the session or connection. |
||||||||||||||
|
Disconnected sessions |
Indicates the number of sessions from which users have disconnected, but which are still active and can be reconnected. |
Number |
Too many disconnected sessions running indefinitely on an AVD cause excessive consumption of the system resources. To avoid this, you can configure a MaxDisconnectionTime in the Windows registry. This will make sure that sessions that remain disconnected beyond the configured period of time automatically end. Additionally, you can set session time limits using the following group policies:
|
||||||||||||||
|
Listen sessions |
Indicates the current number of sessions that are ready to accept connections. |
Number |
|
||||||||||||||
|
Shadow sessions |
Indicates the current number of sessions that are remotely controlling other sessions. |
Number |
A non-zero value for this measure indicates the existence of shadow sessions that are allowed to view and control the user activity on another session. Such sessions help in troubleshooting/resolving problems with other sessions under their control. |
||||||||||||||
|
Down sessions |
Indicates the current number of sessions that could not be initialized or terminated. |
Number |
Ideally, the value of this measure should be 0. By default, if sessions to any of these ports – 65536, 65537, 65538 – could not be initialized or terminated, they will not be counted as a ‘down session’. |
||||||||||||||
|
Init sessions |
Indicates the current number of sessions that are initializing. |
Number |
A high value for this measure could indicate that many sessions are currently experiencing initialization problems. |
||||||||||||||
|
Desktop sessions |
Indicates the number of desktop sessions currently established on the host. |
Number |
|
||||||||||||||
|
Application sessions |
Indicates the number of application sessions currently established on the host. |
Number |
|
||||||||||||||
|
Automation Status |
Indicates the current status of automation actions. |
|
The values that this measure can report and their corresponding numeric values are discussed in the table above:
Note: By default, this measure reports the Measure Values listed in the table above. In the graph of this measure however, the value of this measure is represented using their numeric equivalents only. Use the detailed diagnosis of this measure to find out what automation action was triggered when the session was identified as idle or disconnected session. |
The detailed diagnosis capability of the Established sessions measure, if enabled, lists the active and inactive sessions on the AVD and name of the client asociated with AVD. The session type - whether it is an application session or desktop session - is also indicated.
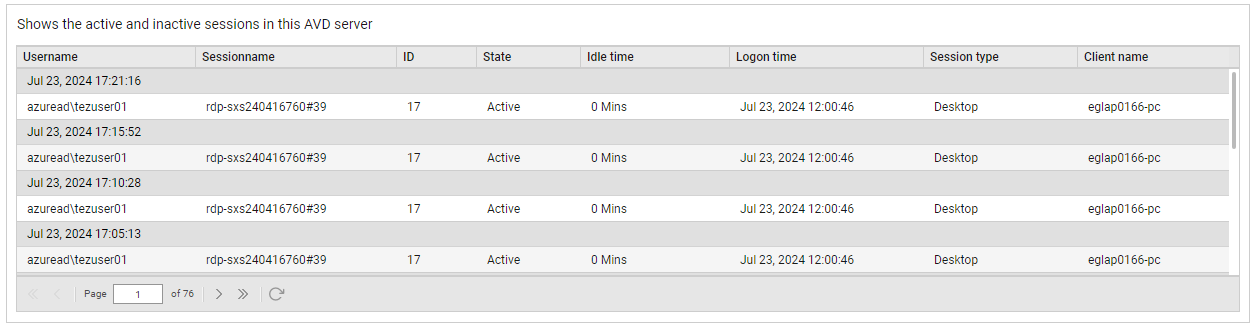
Figure 1 : The detailed diagnosis of the Established sessions measure