Monitoring ISA Proxy Servers
Microsoft Internet Security and Acceleration (ISA) Server can be deployed as a dedicated firewall that acts as the secure gateway to the Internet for internal clients. ISA Server protects all communication between internal computers and the Internet. In a simple firewall scenario, the ISA Server computer has two network interface cards, one connected to the local network and one connected to the Internet. By setting the security access policies, you prevent unauthorized access and malicious content from entering the network. You can also restrict what traffic is allowed for each user and group, application, destination, content type, and schedule.
To assure users of safe and secure access to the Internet, and to shield the network from malicious attacks, the availability and internal health of the ISA Proxy server should be constantly monitored.
The eG Enterprise’s unique ISA Proxy monitoring model (see Figure 1) executes a wide variety of tests on the proxy server to enable administrators to determine the following:
- Does the server take too much time to service firewall requests?
- Is the Web Proxy server functioning optimally?
- Is the Web Proxy Cache utilized effectively?
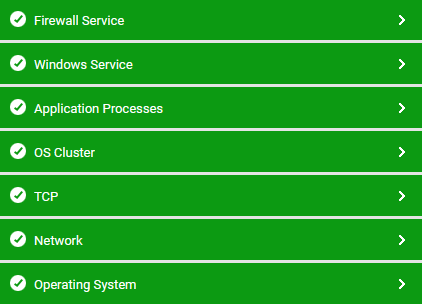
Figure 1 : Layer model of an ISA Proxy server
The sections to come will discuss the tests associated with the Firewall Service layer only, since the remaining layers have already been discussed in the Monitoring Unix and Windows Servers document.