Generating Secret Key for TOTP based User Authentication
In order to generate a secret key for TOTP-based dynamic 2FA, you need to first register your logon simulation endpoint on Microsoft Azure Active Directory (AD). Let us now discuss elaborately on how to register your logon simulation endpoint and generate the secret key using OATH soft token in Microsoft Azure AD in the forthcoming section.
Registering the Logon Simulation Endpoint as an Application to generate OATH Soft token in Microsoft Azure AD
Prior to registering the logon simulation endpoint, you need to download and install an Authenticator App ( for e.g., Microsoft Authenticator, Google Authenticator, Citrix SSO) on your mobile from Android Play Store or Apple Store based on the operating system of your mobile.
If the user who is authorized to perform logon simulation belongs to Microsoft Azure Active Directory, then, you may need to follow the steps mentioned below to register the logon simulation endpoint and generate a secret key/code.
-
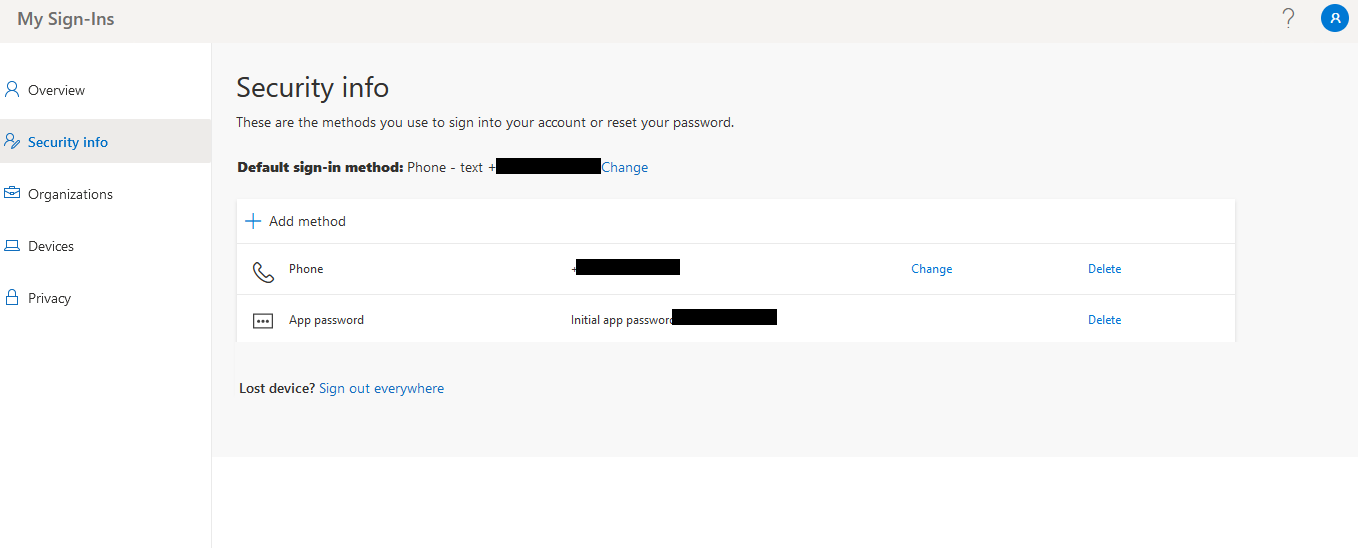
Log in to the URL: https://<Fully Qualified Domain Name of Microsoft Office 365 site in your environment>/securityinfo with the credentials of the user who is authorized to perform logon simulation. Figure 1 then appears.
-
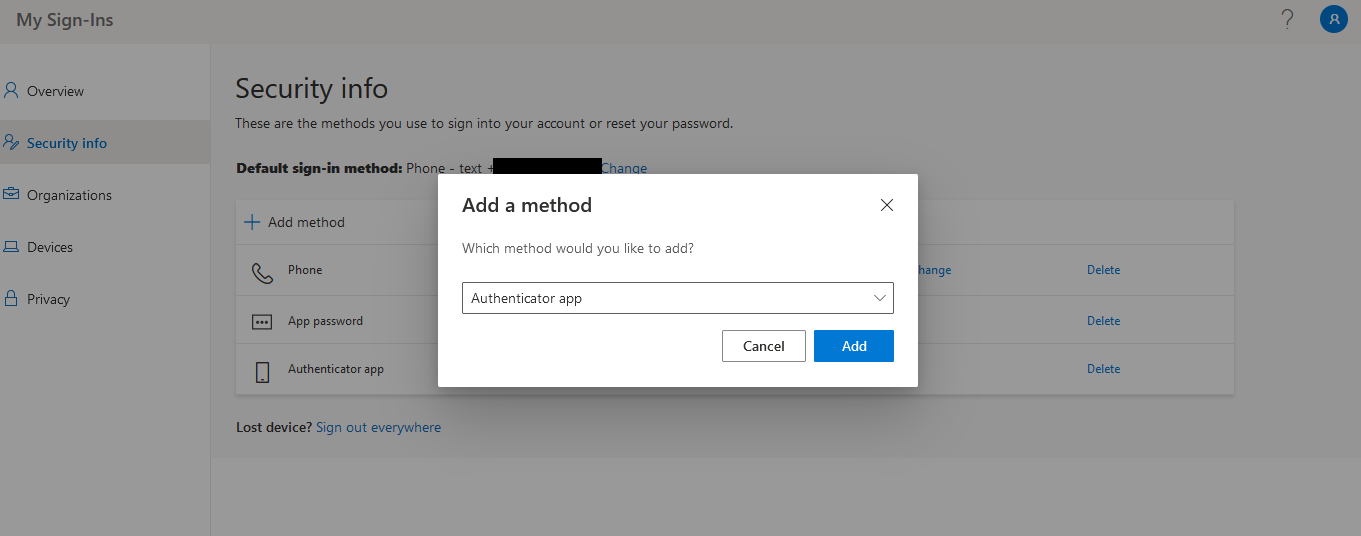
In Figure 1, click the Add method. This will invoke the Add a method pop up window as shown in Figure 2.
-
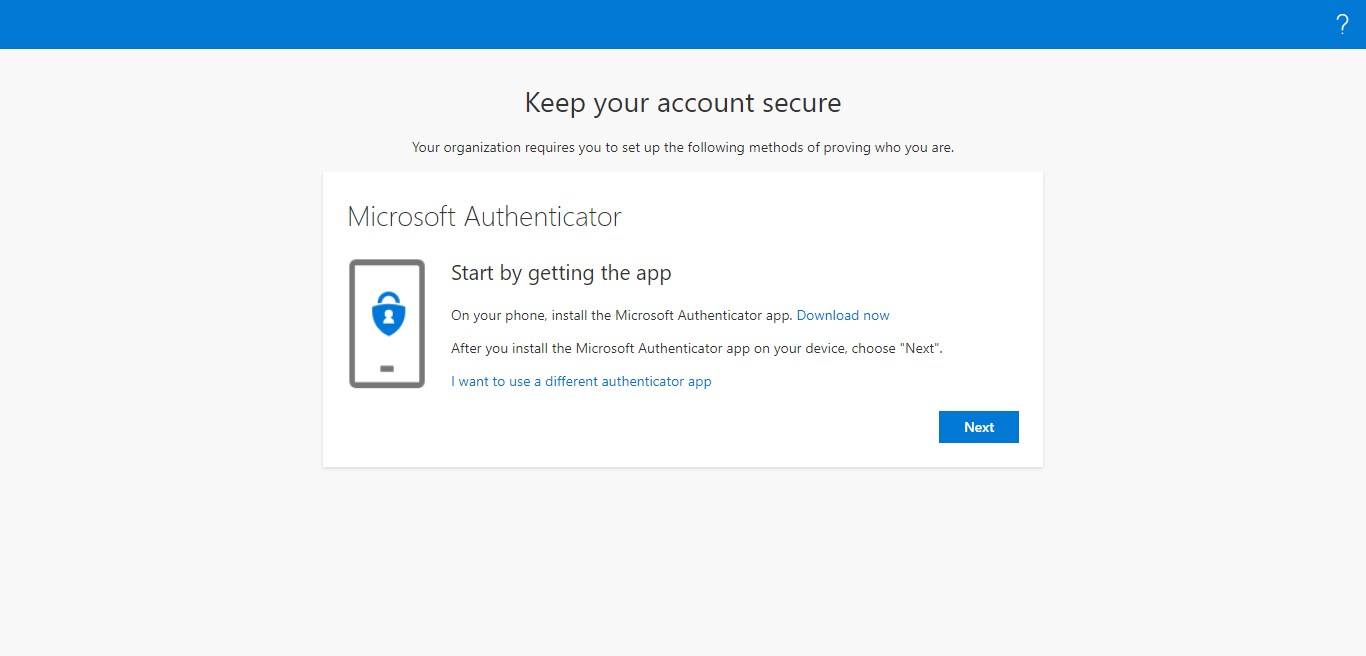
In Figure 2, choose Authenticator App from the Which method would you like to add? drop-down list and click the Add button. Figure 3 then appears.
-
In Figure 3, click the I want to use a different authenticator app link and click the Next button. This will start setting up the account for the authenticator app.
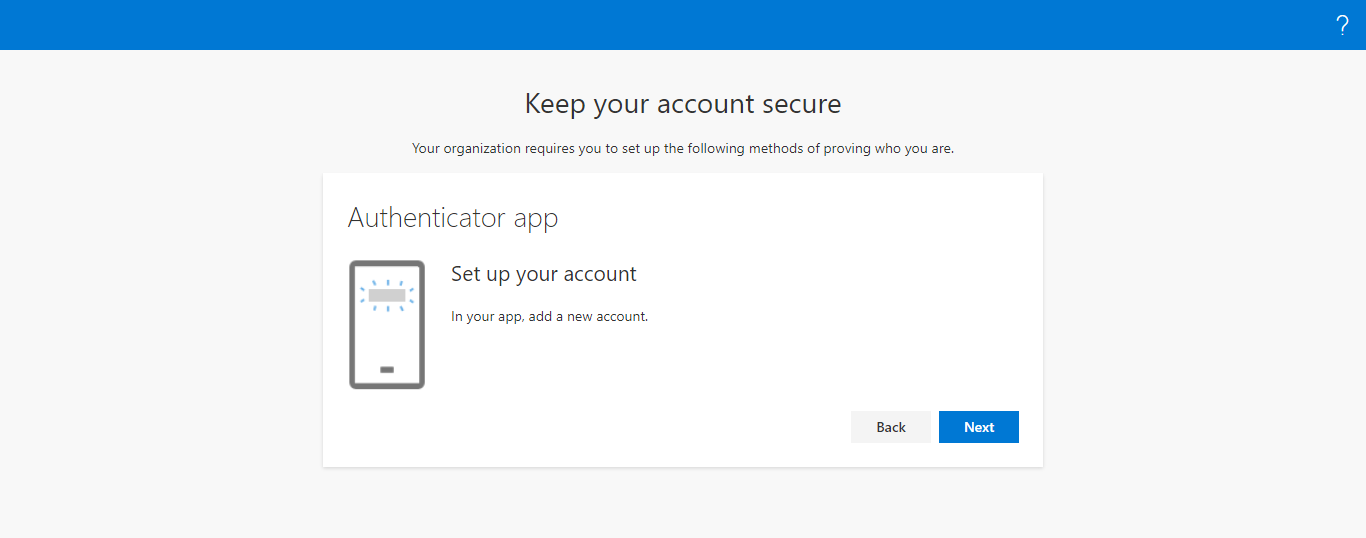
Figure 4 : Setting up your account for a different authenticator app
-
Clicking the Next button in Figure 4 will reveal the QR code and secret key as shown in Figure 5. Ensure that you note down this secret key as this should later be specified in the text box that appears when you set the Is 2FA enabled? flag to Yes while configuring the simulation.
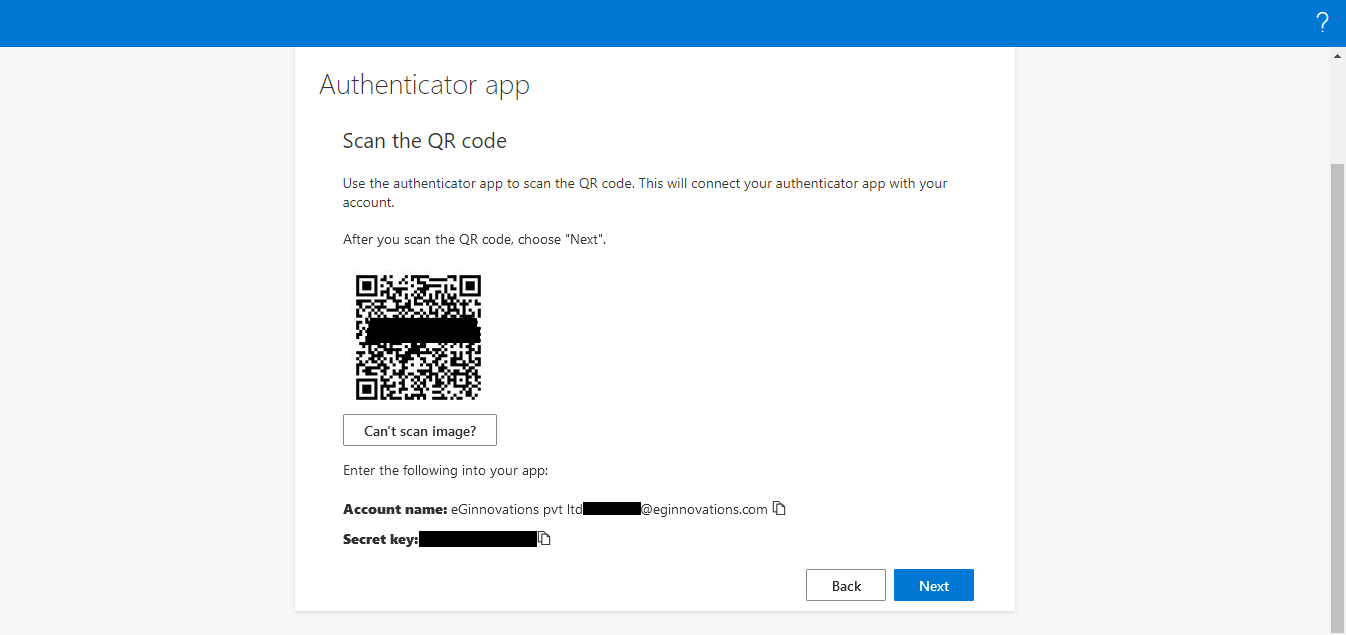
Figure 5 : QR code and secret key displayed for the registered endpoint
-
Clicking the Next button will lead you to Figure 6 where you will be required to enter the passcode generated on your Authenticator App. This is an additional layer of security that is required for registering the logon simulation endpoint. In our example, to generate the passcode, the QR code/Secret Key shown in Figure 5 is scanned using/entered in the Microsoft Authenticator App.
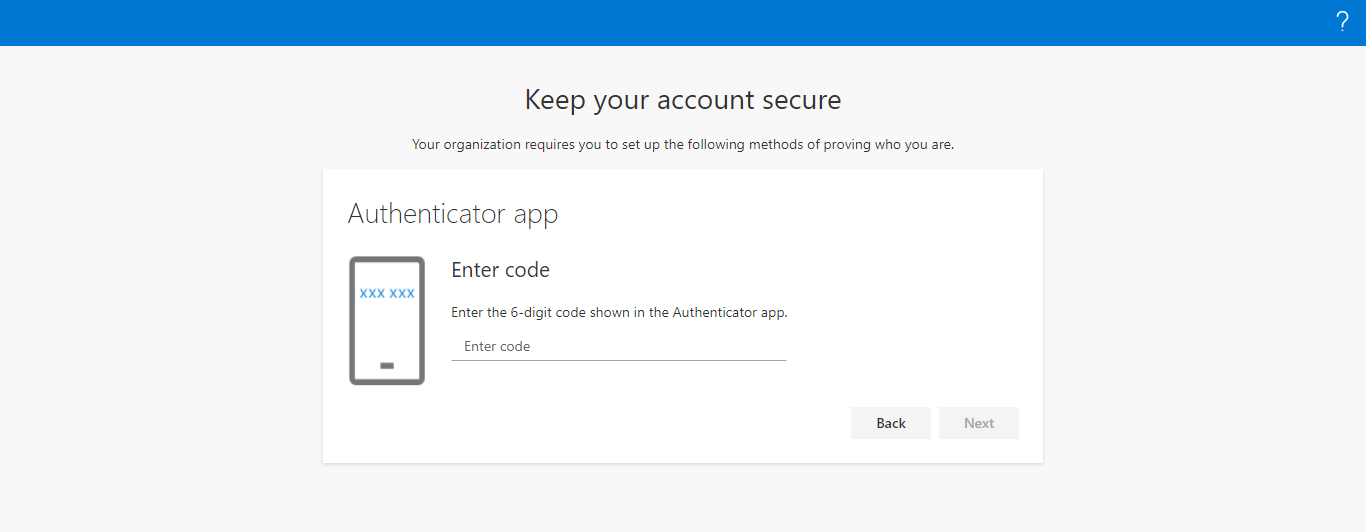
Figure 6 : Authenticating the user credentials with a passcode from the Authenticator App
-
Once the code is specified in Figure 6, clicking the Next button will ensure that your logon simulation endpoint is successfully registered as shown in Figure 7.
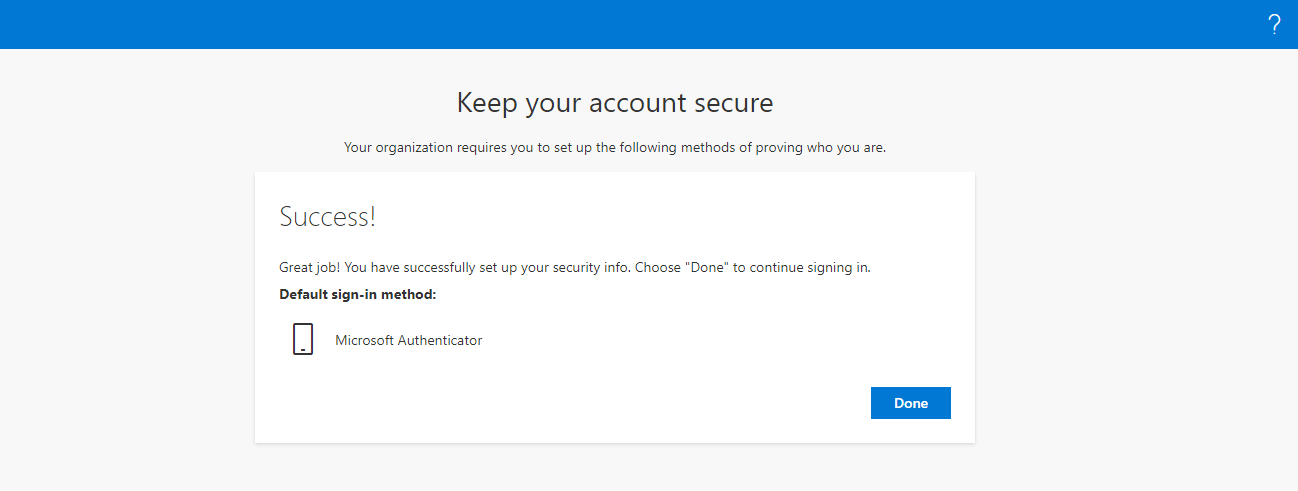
Figure 7 : A message stating that the logon simulation endpoint registration is successful
- Once the logon simulation endpoint registration is successful, you are required to set the Authenticator App as the default sign in method in your Microsoft Office 365 account. For this, you need to navigate to the Security Info page and click the Change link against the Default sign-in method: label (see Figure 8).
-
The Change default method pop up window will then be invoked. Here, select the Authenticator app or hardware token - code option from the Which method would you like to use to sign in? list.
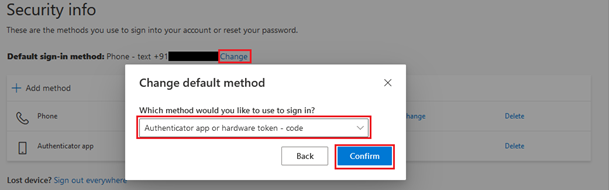
- Clicking the Confirm button will ensure that your logon simulation endpoint is registered and is ready for monitoring.