Azure VPN Gateway Test
A VPN gateway is a specific type of virtual network gateway that is used to send encrypted traffic between an Azure virtual network and an on-premises location over the public Internet. You can also use a VPN gateway to send encrypted traffic between Azure virtual networks over the Microsoft network. Each virtual network can have only one VPN gateway. However, you can create multiple connections to the same VPN gateway.
Needless to say, problems experienced by a VPN gateway can adversely impact network communication and traffic routed by that gateway. Such problems can include the failure of a gateway, excessive bandwidth usage by the tunnels to a gateway, unsuitable configuration of the gateway, error events, packet drops, disconnected routes, and unusually high traffic levels. Administrators should keep an eye on these hot-spots to promptly capture real/potential anomalies and eliminate them, before critical business communication is impacted. This is where the Azure VPN Gateway test helps!
This test monitors each VPN gateway that is configured for a resource group in the target Azure subscription. For every gateway, the test reports the configuration of the gateway, and measures the bandwidth/throughput used by the tunnels of the gateway in real-time, thus indicating to administrators if the configuration fulfills the throughput requirements. Based on these insights, administrators can even decide to switch to a VPN gateway configuration that is ideal for their specific needs. The test also monitors the incoming and outgoing traffic through each VPN gateway, and alerts administrators to potentially abnormal traffic levels. In addition, the test highlights issues that can impede smooth communication over the network such as unexpected gateway failures, packet drops, sudden route disconnects, and revoked certificates. This enables administrators to accurately identify what went wrong and why, so that the appropriate remedial measures can be employed.
Note:
Typically, to consolidate log entries, correlate log data, and perform complex analysis, the resource logs of VPN gateways are often sent to one/more Log Analytics Workspaces. This test reports valid metrics on gateway performance and problems by reading data from these Log Analytics Workspaces only. If the diagnostic logs of VPN gateways are not sent to any Log Analytics Workspace, then this test will only report the value 0 for most of its measures. To avoid this, before configuring this test, make sure that every VPN gateway's diagnostic logs are configured to be sent to at least one Log Analytics Workspace. Follow the steps discussed in Configuring a VPN Gateway's Diagnostic Logs to be Sent to a Log Analytics Workspace to achieve this.
Target of the Test: A Microsoft Azure Subscription
Agent deploying the test: A remote agent
Output of the test: One set of results for each VPN gateway configured in every resource group of the target Azure subscription
| Parameters | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Subscription ID |
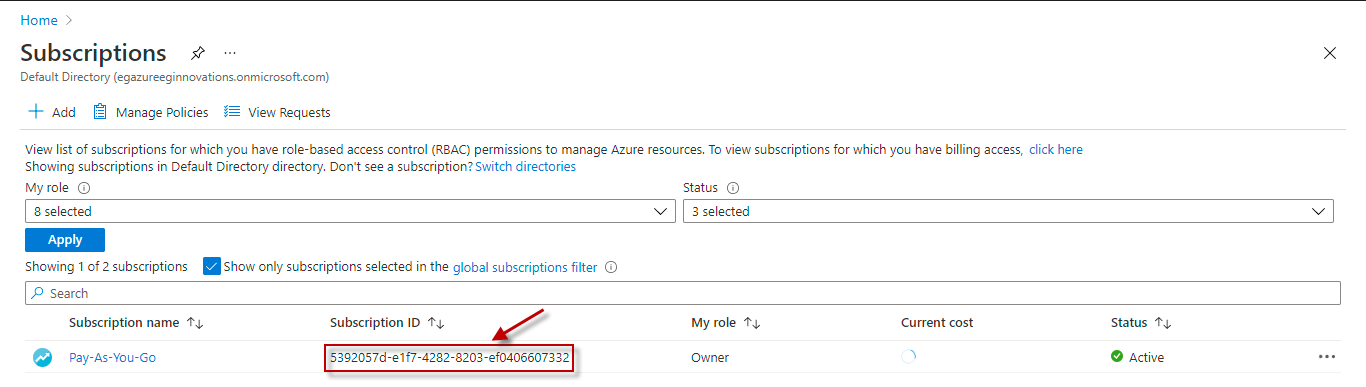
This field will be automatically populated if you have chosen to automatically fulfill the pre-requisites for monitoring the Microsoft Azure Subscription. Specify the GUID which uniquely identifies the Microsoft Azure Subscription to be monitored in this text box
|
|
Tenant ID |
This field will be automatically populated if you have chosen to automatically fulfill the pre-requisites for monitoring the Microsoft Azure Subscription. Specify the Directory ID of the Azure Entra ID tenant to which the target subscription belongs in this text box |
|
Client ID, Client Password, and Confirm Password |
To connect to the target subscription, the eG agent requires an Access token in the form of an Application ID and the client secret value. For this purpose, you should register a new application with the Microsoft Entra tenant. To know how to create such an application and determine its Application ID and client secret, refer to Configuring the eG Agent to Monitor a Microsoft Azure Subscription Using Azure ARM REST API. Specify the Application ID of the created Application in the Client ID text box and the client secret value in the Client Password text box |
|
Proxy Host and Proxy Port |
In some environments, all communication with the Azure cloud be routed through a proxy server. In such environments, you should make sure that the eG agent connects to the cloud via the proxy server and collects metrics. To enable metrics collection via a proxy, specify the IP address of the proxy server and the port at which the server listens against the Proxy Host and Proxy Port parameters. By default, these parameters are set to none, indicating that the eG agent is not configured to communicate via a proxy, by default. |
|
Proxy Username, Proxy Password and Confirm Password |
If the proxy server requires authentication, then, specify a valid proxy user name and password in the Proxy Username and Proxy Password parameters, respectively. Then, confirm the password by retyping it in the Confirm Password text box. |
|
Log Analytics Workspace |
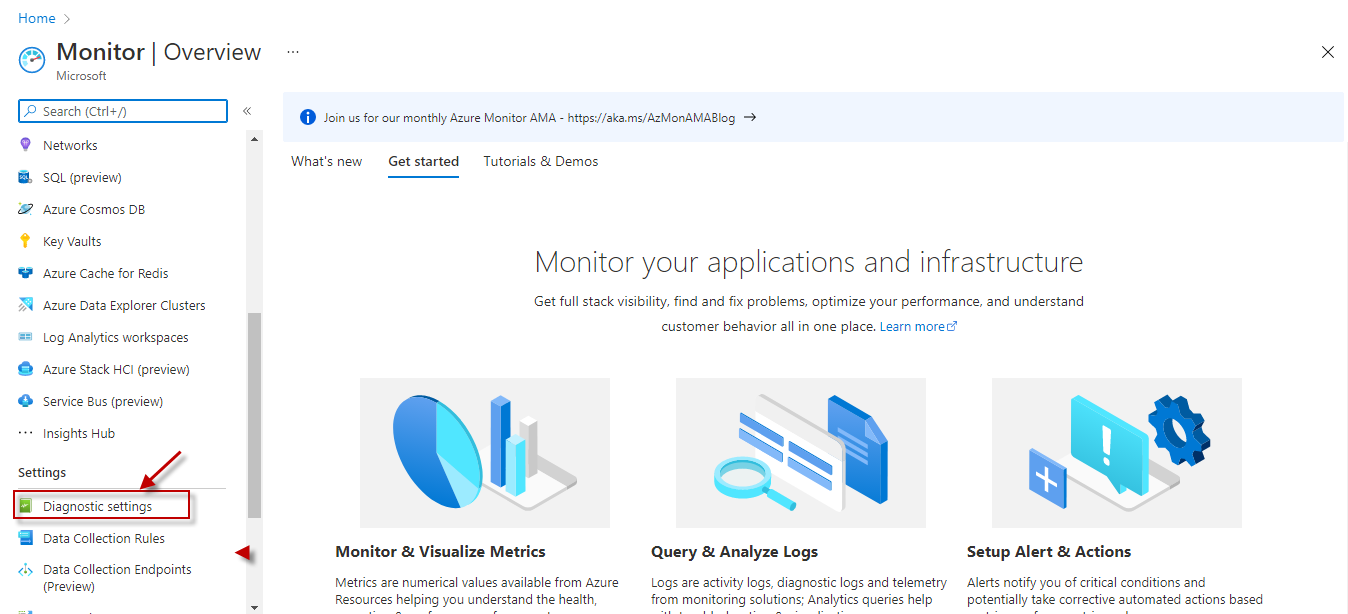
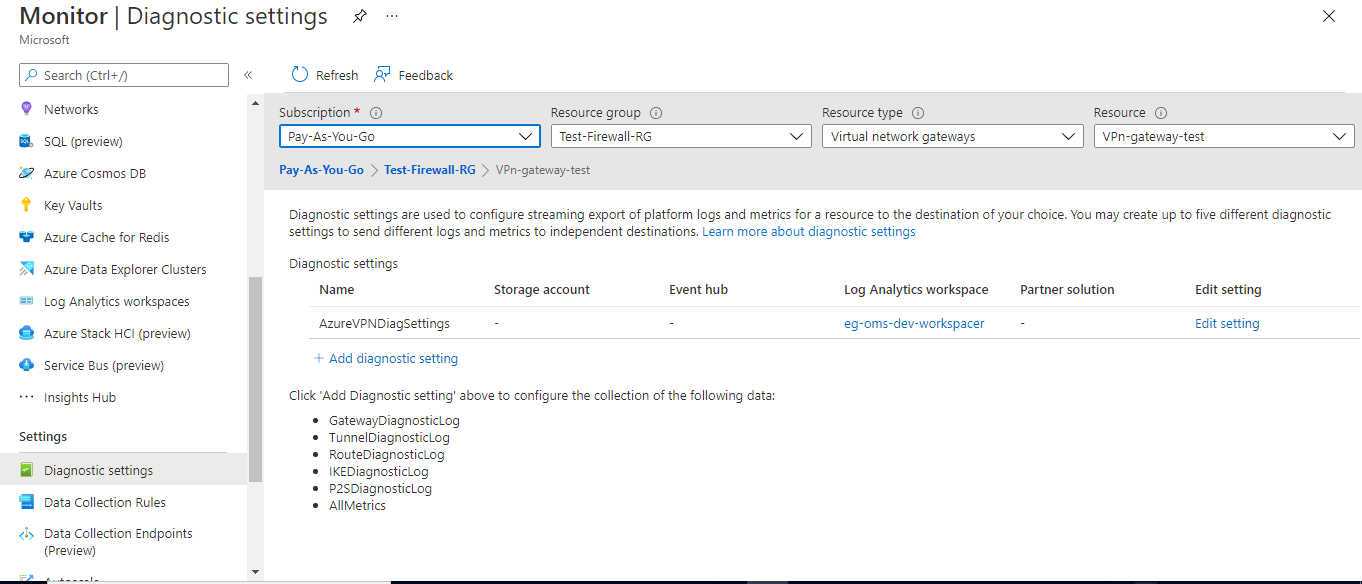
The resource logs pertaining to a VPN gateway can be sent to a designated Log Analytics Workspace, so that administrators can easily consolidate, correlate, and perform complex analysis on the log entries. By default, the Log Analytics Workspace Name parameter is set to All. This indicates that the test reads event data from all Log Analytics Workspaces , by default. However, if you want the test to monitor only those Log Analytics Workspaces to which the diagnostic logs of VPN gateways have been sent, then provide the names of such workspaces here as a comma-separated list. To determine the names of these workspaces, do the following:
Figure 3 : Selecting the Diagnostic Settings option of the Azure Monitor
|
|
Gateway Success DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the Gateway success events measure. If you want to know the details of gateway connections established successfully, then set this flag to True. |
|
Gateway Failed DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the Gateway failed events measure. If you want to know the details of gateway connections that failed, then set this flag to True. |
|
Tunnel Connected DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the Tunnels connected measure. If you want to know the details of all the tunnels that are connected to each VPN gateway, then set this flag to True. |
|
Tunnel Disconnected DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the Tunnels disconnected measure. If you want to know the details of all the tunnels that are disconnected from each VPN gateway, then set this flag to True. |
|
Routes Connected DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the Routes connected measure. If you want to know the details of all the routes that are connected to each VPN gateway, then set this flag to True. |
|
Routes Disconnected DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the Routes disconnected measure. If you want to know the details of all the routes that are disconnected from each VPN gateway, then set this flag to True. |
|
Routes Updates DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the Route updates measure. If you want to know the details of all the routes that are updated, then set this flag to True. |
|
P2S Events DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the P2S events measure. If you want to view the complete list of Point-to-Site control messages and events on each VPN gateway, then set this flag to True. |
|
IKE Events DD |
By default, this flag is set to False. This means that by default, this test does not report detailed diagnosis for the IKE events measure. If you want to view the complete list of IKE control messages and events on each VPN gateway, then set this flag to True. |
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
|
Measurement |
Description |
Measurement Unit |
Interpretation |
||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Provisioning state |
Indicates the current provisioning state of this VPN gateway. |
|
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate the current provisioning state of this VPN gateway. In the graph of this measure however, the same is represented using the numeric equivalents only. Use the detailed diagnosis of this measure to know the resource GUID, location,SKU, tier capacity, and etag of the VPN gateway. |
||||||||||||
|
Gateway types |
Indicates the type of this gateway. |
|
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate the type of gateway. In the graph of this measure however, the same is represented using the numeric equivalents only. |
||||||||||||
|
VPN types |
Indicates the type of this VPN. |
Number |
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate the type of VPN. In the graph of this measure however, the same is represented using the numeric equivalents only. |
||||||||||||
|
Gateway generations |
Indicates this VPN gateway's generation |
|
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate the generation this VPN gateway belongs to. In the graph of this measure however, the same is represented using the numeric equivalents only. |
||||||||||||
|
Is BGP enabled? |
Indicates if the BGP feature is enabled for this VPN gateway. |
|
BGP is the standard routing protocol commonly used in the Internet to exchange routing and reachability information between two or more networks. When used in the context of Azure Virtual Networks, BGP enables the Azure VPN Gateways and your on-premises VPN devices, called BGP peers or neighbors, to exchange "routes" that will inform both gateways on the availability and reachability for those prefixes to go through the gateways or routers involved. BGP can also enable transit routing among multiple networks by propagating routes a BGP gateway learns from one BGP peer to all other BGP peers. The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate whether/not BGP is enabled for a VPN gateway. In the graph of this measure however, the same is represented using the numeric equivalents only. |
||||||||||||
|
Is private IP enabled? |
Indicates whether/not private IPs are enabled on this VPN gateway. |
|
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate whether/not private IPs are enabled on a VPN gateway. In the graph of this measure however, the same is represented using the numeric equivalents only. |
||||||||||||
|
Is activeActive flag enabled? |
Indicates whether/not this VPN gateway is created in an Active-Active configuration. |
|
You can create an Azure VPN gateway in an active-active configuration, where both instances of the gateway VMs will establish S2S VPN tunnels. Because the Azure gateway instances are in active-active configuration, the traffic from your Azure virtual network to your on-premises network will be routed through both tunnels simultaneously, even if your on-premises VPN device may favor one tunnel over the other. When a planned maintenance or unplanned event happens to one gateway instance, the IPsec tunnel from that instance to your on-premises VPN device will be disconnected. The corresponding routes on your VPN devices should be removed or withdrawn automatically so that the traffic will be switched over to the other active IPsec tunnel. On the Azure side, the switch over will happen automatically from the affected instance to the active instance. The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate whether/not the gateway is created in an Active-Active configuration. In the graph of this measure however, the same is represented using the numeric equivalents only. |
||||||||||||
|
Total IPs configured |
Indicates the number of IPs configured on this VPN gateway. |
Number |
Use the detailed diagnosis of this measure to view the private IPs that have been configured on the gateway, the public IPs that map to each, the location, the SKU, the tier, allocation mode, and idle time of every private IP. |
||||||||||||
|
Client root certificates |
Indicates the number of root certificates that this VPN gateway uses to authenticate clients connecting to it. |
Number |
Certificates are used by Azure to authenticate clients connecting to a VNet over a Point-to-Site VPN connection. Once you obtain a root certificate, you upload the public key information to Azure. The root certificate is then considered 'trusted' by Azure for connection over P2S to the virtual network. You also generate client certificates from the trusted root certificate, and then install them on each client computer. The client certificate is used to authenticate the client when it initiates a connection to the VNet. Use the detailed diagnosis of this measure to know the name, state, and public certificate associated with every root certificate used by a gateway. |
||||||||||||
|
Client revoked certificates |
Indicates the number of client certificates that are revoked for this VPN gateway. |
Number |
You can revoke client certificates. The certificate revocation list allows you to selectively deny Point-to-Site connectivity based on individual client certificates. This is different than removing a trusted root certificate. If you remove a trusted root certificate .cer from Azure, it revokes the access for all client certificates generated/signed by the revoked root certificate. Revoking a client certificate, rather than the root certificate, allows the other certificates that were generated from the root certificate to continue to be used for authentication. Use the detailed diagnosis of this measure to know the name, state, and public certificate associated with every client certificate that is revoked. |
||||||||||||
|
Client IPsec policies |
Indicates the number of IPsec policies created for this VPN gateway. |
Number |
VPN gateways use IPsec policies for Site-to-Site VPN or VNet-to-VNet connections using the Azure portal. Use the detailed diagnosis of this measure to view the complete information related to the IPsec policies created for a gateway. |
||||||||||||
|
Radius servers |
Indicates the number of RADIUS servers used for authenticating P2S (Point-to-Site) connections via this VPN gateway. |
Number |
Using the detailed diagnosis of this measure, you can determine the address and score of each RADIUS server used for authenticating P2S connections. |
||||||||||||
|
Client protocols |
Indicates the number of client protocols supported by this VPN gateway. |
Number |
The detailed diagnosis of this measure lists the client protocols supported by the gateway. |
||||||||||||
|
Authentication types |
Indicates the number of authentication types supported by this VPN gateway. |
Number |
The detailed diagnosis of this measure lists the authentication types supported by the gateway. |
||||||||||||
|
Gateway P2S bandwidth |
Indicates the average combined bandwidth utilization of all point-to-site connections on this gateway. |
KB/Sec |
Throughput is the rate that data is sent through the VPN Gateway. VPN Gateways have different throughput benchmarks depending on the gateway type and SKU. Both Site-to-Site (S2S) and Point-to-Site (P2S) connections share the same bandwidth on a VPN gateway, so increased usage from one type of connection can impact the performance of the other type. Hitting the maximum throughput on a VPN Gateway can be an indication that you should look at your network to either decrease throughput requirements, or increase the capacity of the gateway. |
||||||||||||
|
Gateway S2S bandwidth |
Indicates the average combined bandwidth utilization of all site-to-site connections on this gateway. |
KB/Sec |
|||||||||||||
|
P2S connections count |
Indicates the number of point-to-site connections on this gateway. |
Number |
Azure VPN Gateways limit the number of Point-to-Site (P2S) connections allowed to a single gateway. Depending on their SKU, VPN Gateways can be configured to allow connections using these protocols:
SSTP Connections are limited to 128 concurrent connections for all VPN Gateway SKUs. There is not a way to increase this limit, but most VPN clients will support one of the other protocols so connecting over a different protocol may help avoid the limit. OpenVPN and IKEv2 connections are limited together and together have a higher limit than SSTP connections. Hitting the limit on the number of connections will prevent additional connections from succeeding. This can impact your employee by not allowing them access to the network when it is needed. If you are hitting P2S connection limits frequently, you may consider implementing a policy such that your employees only connect when they need access to the virtual network, or you can upgrade your gateway to allow for more connections or set up multiple gateways. |
||||||||||||
|
Tunnels bandwidth |
Indicates the average bandwidth utilization of tunnels created on this gateway. |
KB/Sec |
When you create a virtual network gateway, you specify the gateway SKU that you want to use. Select the SKU that satisfies your requirements based on the types of workloads, throughputs, features, and SLAs. Aggregate Throughput Benchmark for a VPN Generation:SKU combination is based on measurements of multiple tunnels aggregated through a single gateway. The Aggregate Throughput Benchmark for a VPN Gateway is S2S + P2S combined. If the value of this measure is consistently close to the Aggregate Throughput Benchmark, it means that SKU chosen may not be able to fulfill the application throughput requirements of the gateway. You may want to consider choosing a different SKU for the gateway in this case. |
||||||||||||
|
Egress traffic |
Indicates the traffic flowing out of the tunnels created on this gateway. |
KB |
If the value of the Tunnel bandwidth measure is abnormally high for a gateway, you may want to compare the value of these measures to figure out if the unusual bandwidth consumption is owing to incoming or outgoing traffic.
|
||||||||||||
|
Ingress traffic |
Indicates the traffic flowing into the tunnels created on this gateway. |
KB |
|||||||||||||
|
Egress packets |
Indicates the number of outgoing packets for this gateway. |
Number |
If the value of the Tunnel bandwidth measure is abnormally high for a gateway, you may want to compare the value of these measures to figure out if the unusual bandwidth consumption is owing to incoming or outgoing traffic.
|
||||||||||||
|
Ingress packets |
Indicates the number of incoming packets for this gateway. |
Number |
|||||||||||||
|
Egress TS mismatch packet drops |
Indicates the number of outgoing packets dropped by tunnels on this gateway, because of a traffic-selector mismatch. |
Number |
Traffic selector mismatch occurs when the local and remote addresses for traffic in the VPN tunnel does not match the traffic selectors configured on either end of the VPN. Traffic selector mismatch is caused by configuration on either end of the VPN tunnel. Azure VPN Gateways support specific IPsec and IKE configurations that must match with the device on the other end of the tunnel. Ideally therefore, the value of these measures should be 0. |
||||||||||||
|
Ingress TS mismatch packet drops |
Indicates the number of incoming packets dropped by tunnels on this gateway, because of a traffic-selector mismatch. |
Number |
|||||||||||||
|
NAT allocations |
Indicates the number of NAT ports allocated by this gateway. |
Number |
|
||||||||||||
|
NAT flows |
Indicates the number of outbound traffic flows provided by this gateway. |
Number |
NAT gateway provides outbound internet connectivity for one or more subnets of a virtual network. Once NAT gateway is associated to a subnet, NAT provides source network address translation (SNAT) for that subnet. NAT gateway specifies which static IP addresses virtual machines use when creating outbound flows. Each NAT gateway can support 64,000 flows each for TCP and UDP per assigned outbound IP address. |
||||||||||||
|
NATed traffic |
Indicates the number of bytes processed inbound and outbound by this gateway. |
KB |
|
||||||||||||
|
Reverse NATed traffic |
Indicates the data traffic - inbound and outbound - over reverse NAT. |
KB |
Reverse NAT is a specific sub-type of Static NAT. It refers to the translation of a Public IP (For example on the DSL Router) to a Private IP (User PC). Since the direction is 'Reverse' its called Reverse NAT. |
||||||||||||
|
NATed packets |
Indicates the number of packets processed inbound and outbound by this gateway. |
Number |
|
||||||||||||
|
Reverse NATed packets |
Indicates the number of packets processed - inbound and outbound - over reverse NAT. |
Number |
|
||||||||||||
|
NAT packet drops |
Indicates the number of packets dropped by this NAT gateway. |
Number |
Ideally, the value of this measure should be 0. |
||||||||||||
|
Gateway success events |
Indicates the number of events logged in the GatewayDiagnosticLog of this gateway, which are tagged as successful. |
Number |
Configuration changes are audited in the GatewayDiagnosticLog. The events that trigger such changes are: SetGatewayConfiguration, SetConnectionConfiguration, HostMaintenanceEvent, GatewayTenantPrimaryChanged, MigrateCustomerSubscription, GatewayResourceMove, ValidateGatewayConfiguration Use the detailed diagnosis of this measure to know which configuration changes triggered successful change events. Note that this measure will report detailed metrics only if the GATEWAY SUCCESS DD flag of this test is set to True. |
||||||||||||
|
Gateway failed events |
Indicates the number of events logged in the GatewayDiagnosticLog of this gateway, which are tagged as failed. |
Number |
Ideally, the value of this measure should be 0. Use the detailed diagnosis of this measure to know which configuration changes failed to be effected on the gateway. Note that this measure will report detailed metrics only if the GATEWAY FAILED DD flag of this test is set to True. |
||||||||||||
|
Tunnels connected |
Indicates the number of TunnelConnected events logged in the TunnelDiagnosticLog of this gateway. |
Number |
For details of all the TunnelConnected events logged in the TunnelDiagnosticLog, use the detailed diagnosis of this measure. Note that this measure will report detailed metrics only if the TUNNEL CONNECTED DD flag of this test is set to True. |
||||||||||||
|
Tunnels disconnected |
Indicates the number of TunnelDisconnected events logged in the TunnelDiagnosticLog of this gateway. |
Number |
Ideally, the value of this measure should be 0. For details of all the TunnelDisconnected events logged in the TunnelDiagnosticLog, use the detailed diagnosis of this measure. Note that this measure will report detailed metrics only if the TUNNEL DISCONNECTED DD flag of this test is set to True. |
||||||||||||
|
Routes connected |
Indicates the number of BgpConnectedEvent events logged in the RouteDiagnosticLog of this gateway. |
Number |
For details of all the BgpConnected events logged in the RouteDiagnosticLog, use the detailed diagnosis of this measure. Note that this measure will report detailed metrics only if the ROUTES CONNECTED DD flag of this test is set to True. |
||||||||||||
|
Routes disconnected |
Indicates the number of BgpDisconnectedEvent events logged in the RouteDiagnosticLog of this gateway. |
Number |
Ideally, the value of this measure should be 0. For details of all the BgpDisconnected events logged in the RouteDiagnosticLog, use the detailed diagnosis of this measure. Note that this measure will report detailed metrics only if the ROUTES DISCONNECTED DD flag of this test is set to True. |
||||||||||||
|
Route updates |
Indicates the number of StaticRouteUpdate and BgpRouteUpdate events logged in the RouteDiagnosticLog of this gateway. |
Number |
For details of all the StaticRouteUpdate and BgpRouteUpdate events logged in the RouteDiagnosticLog, use the detailed diagnosis of this measure. Note that this measure will report detailed metrics only if the ROUTES UPDATES DD flag of this test is set to True |
||||||||||||
|
P2S events |
Indicates the number of P2SLogEvent events logged in the P2SDiagnosticLog of this gateway. |
Number |
For details of all the P2SLogEvent events logged in the P2SDiagnosticLog, use the detailed diagnosis of this measure. Note that this measure will report detailed metrics only if the P2S EVENTS DD flag of this test is set to True |
||||||||||||
|
IKE events |
Indicates the number of events logged in the IKEDiagnosticLog of this gateway. |
Number |
For details of all the events logged in the IKEDiagnosticLog, use the detailed diagnosis of this measure. Note that this measure will report detailed metrics only if the IKE EVENTS DD flag of this test is set to True |
Use the detailed diagnosis of the Total IPs configured measure to view the private IPs that have been configured on the gateway, the public IPs that map to each, the location, the SKU, the tier, allocation mode, and idle time of every private IP.
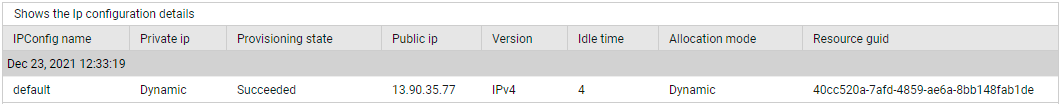
Figure 6 : The detailed diagnosis of the Total IPs configured measure