Azure Virtual Network Test
Azure Virtual Network is a fundamental service in Microsoft Azure that enables the administrators to build and operate a logically isolated network in the Azure cloud. It helps the administrators to connect Azure resources securely, define network topologies, and control network traffic, leading to a secure and flexible network environment for Azure applications and services.
If the Virtual Network encounters problems or fails, then VMs, databases, and other Azure resources in the Virtual Network loses communication with each other. Virtual network uses TCP that provides a retransmission mechanism to retrieve packets that have been lost. Using this test, the administrators can monitor the dropped TCP packets that leads to higher latency, reduced throughput, decreased application performance, and increased resource utilization.
Virtual Network can be affected by a DDoS attack, which is a malicious attempt to overload Azure-based resources, such as virtual machines, web applications or other Azure services with an excessive volume of traffic. Using this test, the administrators can detect the DDoS attack at early stages and take preventive measures to mitigate their effects before they cause significant service disruption.
Target of the Test : A Microsoft Azure Subscription
Agent deploying the test: A remote agent
Output of the test: One set of results for each resource group:virtual network in the target Microsoft Azure Subscription
| Parameters | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Subscription ID |
This field will be automatically populated if you have chosen to automatically fulfill the pre-requisites for monitoring the Microsoft Azure Subscription. Specify the GUID which uniquely identifies the Microsoft Azure Subscription to be monitored in this text box
|
|
Tenant ID |
This field will be automatically populated if you have chosen to automatically fulfill the pre-requisites for monitoring the Microsoft Azure Subscription. Specify the Directory ID of the Azure Entra ID tenant to which the target subscription belongs in this text box |
|
Client ID, Client Password, and Confirm Password |
To connect to the target subscription, the eG agent requires an Access token in the form of an Application ID and the client secret value. For this purpose, you should register a new application with the Microsoft Entra tenant. To know how to create such an application and determine its Application ID and client secret, refer to Configuring the eG Agent to Monitor a Microsoft Azure Subscription Using Azure ARM REST API. Specify the Application ID of the created Application in the Client ID text box and the client secret value in the Client Password text box |
|
Proxy Host and Proxy Port |
In some environments, all communication with the Azure cloud be routed through a proxy server. In such environments, you should make sure that the eG agent connects to the cloud via the proxy server and collects metrics. To enable metrics collection via a proxy, specify the IP address of the proxy server and the port at which the server listens against the Proxy Host and Proxy Port parameters. By default, these parameters are set to none, indicating that the eG agent is not configured to communicate via a proxy, by default. |
|
Proxy Username, Proxy Password and Confirm Password |
If the proxy server requires authentication, then, specify a valid proxy user name and password in the Proxy Username and Proxy Password parameters, respectively. Then, confirm the password by retyping it in the Confirm Password text box. |
|
DD Frequency |
Refers to the frequency with which detailed diagnosis measures are to be generated for this test. The default is 1:1. This indicates that, by default, detailed measures will be generated every time this test runs, and also every time the test detects a problem. You can modify this frequency, if you so desire. Also, if you intend to disable the detailed diagnosis capability for this test, you can do so by specifying none against DD frequency. |
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
| Measurement | Description | Measurement Unit | Interpretation | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Provisioning state |
Indicates the provisioning state of this virtual network. |
|
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate provisioning state of this virtual network. In the graph of this measure however, the same is represented using the numeric equivalents only. Use the detailed diagnosis of this measure to know Location, Address prefix, and Enable Ddos protection details associated to the virtual network. |
||||||||||
|
VMs attached to this virtual network |
Indicates the number of virtual machines managed by this virtual network. |
Number |
|
||||||||||
|
Packets forwarded |
Indicates the number of TCP and UDP packets forwarded by this virtual network. |
Number |
|
||||||||||
|
TCP packets |
Indicates the number of TCP packets involved in data transmission by virtual network. |
Number |
|
||||||||||
|
Total dropped TCP packets |
Indicates the total number of TCP packets dropped in this virtual network. |
Number |
TCP packet drop refers to loss of data packets in a TCP connection. Increased TCP packet drops in virtual network can result in higher latency, reduced throughput, decreased application performance, and increased resource utilization. |
||||||||||
|
Total forwarded TCP packets |
Indicates the total number of TCP packets forwarded by this virtual network. |
Number |
|
||||||||||
|
UDP packets |
Indicates the number of UDP packets associated to this virtual network. |
Number |
UDP is a protocol used for applications that require low-latency and high-speed data transmission within an Azure Virtual Network but unlike TCP, it lacks in handling packet loss or errors. |
||||||||||
|
Total dropped UDP packets |
Indicates the total number of UDP packets dropped in this virtual network. |
Number |
|
||||||||||
|
Total forwarded UDP packets |
Indicates the total number of UDP packets forwarded by this virtual network. |
Number |
|
||||||||||
|
Packets data |
Indicates the amount of TCP and UDP packets in this virtual network. |
Bytes |
|
||||||||||
|
Packets dropped data |
Indicates the amount of TCP and UDP packets dropped in this virtual network. |
Bytes |
|
||||||||||
|
Packets forwarded data |
Indicates the amount of TCP and UDP packets forwarded by this virtual network. |
Bytes |
|
||||||||||
|
TCP packets data |
Indicates the amount of TCP packets involved in data transmission by this virtual network. |
Bytes |
|
||||||||||
|
TCP packets dropped data |
Indicates the amount of TCP packets dropped in this virtual network. |
Bytes |
|
||||||||||
|
TCP packets forwarded data |
Indicates the amount of TCP packets forwarded by this virtual network. |
Bytes |
|
||||||||||
|
UDP packets data |
Indicates the amount of UDP packets involved in data transmission by this virtual network. |
Bytes |
|
||||||||||
|
UDP packets dropped data |
Indicates the amount of UDP packets dropped in this virtual network. |
Bytes |
|
||||||||||
|
UDP packets forwarded data |
Indicates the amount of UDP packets forwarded by this virtual network. |
Bytes |
|
||||||||||
|
DDoS attack is happening or not |
Indicates whether/not Distributed Denial of Service (DDoS) attack has occurred in this virtual network. |
|
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate whether/not DDoS attack has occurred in the virtual network. The graph of this measure however, represents the status of DDoS attack using the numeric equivalents only i.e., 0 or 1. |
||||||||||
|
DDoS mitigation triggered by TCP packets |
Indicates the number of TCP packets that mitigate DDoS attacks. |
Number |
TCP requires a three-way Handshake (SYN, SYN-ACK, ACK) to establish a network connection that makes it difficult for attackers to simply flood the servers with requests without going through the Handshake process, as they must properly respond to the server's SYN-ACK.
|
||||||||||
|
DDoS mitigation triggered by SYN packets |
Indicates the number of SYN packets that mitigate DDoS attacks. |
Number |
|||||||||||
|
DDoS mitigation triggered by UDP packets |
Indicates the number of UDP packets that mitigate DDoS attacks. |
Number |
Network devices can implement rate limiting on UDP packets to restrict the number of incoming requests from a single source. This helps prevent overwhelming the server during an attack. |
||||||||||
|
Average Ping RTT of VMs |
Indicates the average ping round-trip time taken by network packet to travel from a source VM to a destination VM and vice-versa. |
Seconds |
|
||||||||||
|
Failed Pings to VMs |
Indicates the percentage of pings that failed for the network packet to travel from a source VM to a destination VM. |
Percent |
|
||||||||||
|
Total packets |
Indicates the total number of packets in this vrtual network. |
Number |
|
||||||||||
|
Packets dropped |
Indicates the total number of packets dropped in this vrtual network. |
Number |
|
||||||||||
|
Total subnets |
Indicates the total number of subnets in this vrtual network. |
Number |
|
Use the detailed diagnosis of the Provisioning state measure to know Location, Address prefix and Enable Ddos protection details associated to the virtual network.
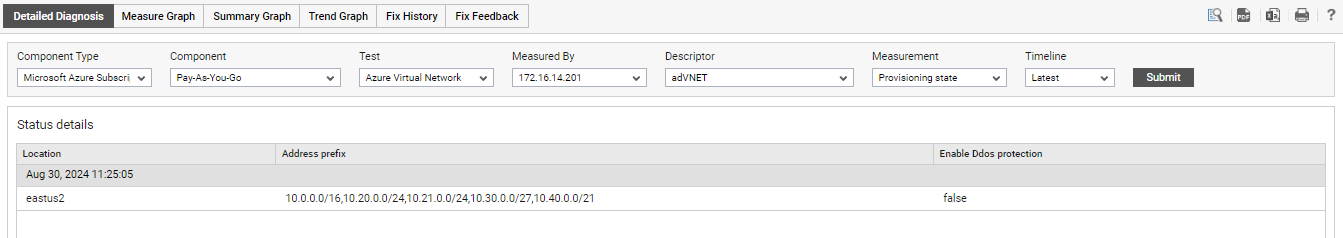
Figure 3 : The detailed diagnosis of the Provisioning state measure