Configuring the Firewall Logs to be Sent to a Log Analytics Workspace
It is recommended that you create a new Log Analytics Workspace for monitoring purposes, and send all the logs that eG monitors to that workspace. If such a workspace pre-exists, then proceed to set that workspace as the destination for firewall logs. To achieve this, use steps 5-10 of the procedure detailed below. If no such workspace is available, then do the following:
-
Use steps 1-4 of the procedure discussed below to create a new log analytics workspace.
-
Then, use steps 5-10 of the procedure to configure the firewall logs to be sent to the new workspace you created.
-
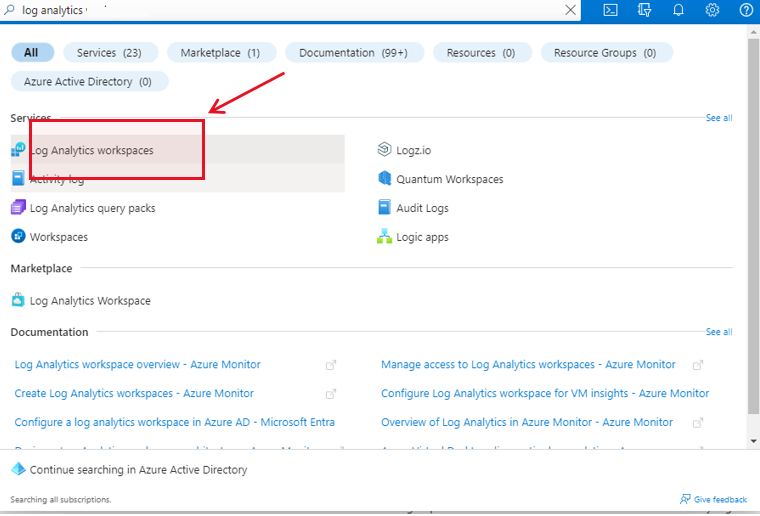
To create a new Log Analytics Workspace, first, login to the Microsoft Azure Portal, and use the Search text box therein to search for the string 'log analytics'. The Log Analytics Workspace option will then appear in the search results (see Figure 1). Click on that option.
-
Figure 2 will then appear. If one/more Log Analytics Workspaces pre-exist, then Figure 2 will reveal them. To create a new workspace, click on the Create link indicated by Figure 2.
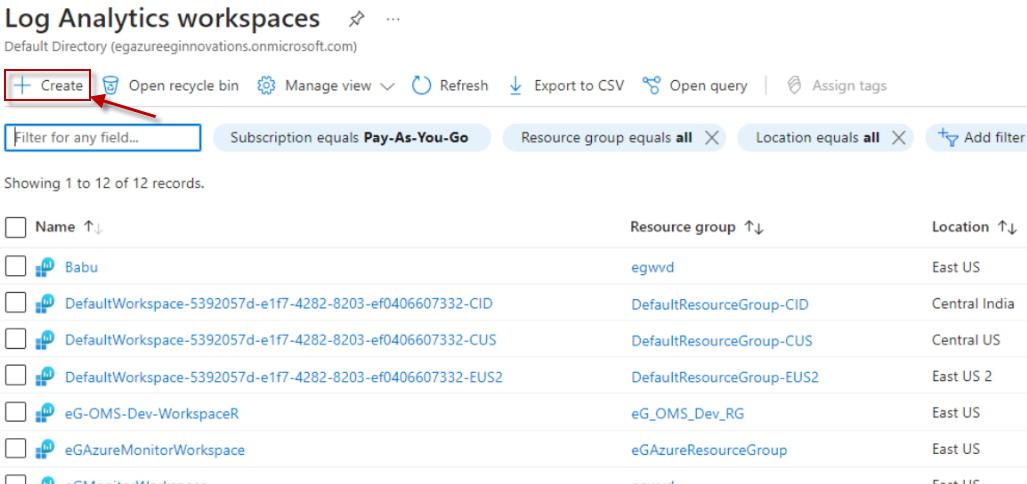
Figure 2 : Clicking on the Create link in the Log Analytics Workspaces window
-
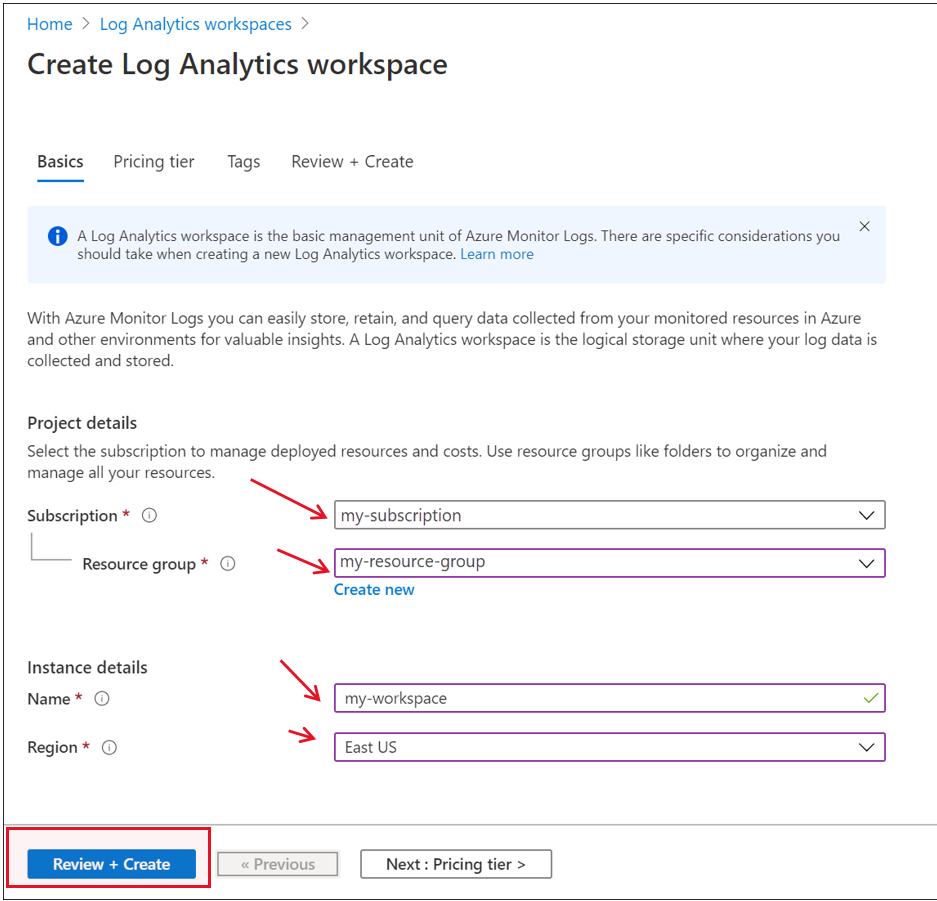
Doing so will invoke Figure 3. From the Subscription drop-down in Figure 3, select the Azure Subscription for which the new workspace is being created. This should be the Microsoft Azure Subscription that you are monitoring. Next, select the Resource Group to which the chosen subscription belongs, and its Region. Finally, specify Name of the new Log Analytics Workspace.
-
Finally, click the Review + Create button to add the new log analytics workspace.
-
Now, proceed to set this workspace as the destination for firewall logs. For that, open your firewall resource group, and select the firewall that you are monitoring.
-
Under Monitoring, select Diagnostic settings.
For Azure Firewall, three service-specific logs are available:
-
AzureFirewallApplicationRule
-
AzureFirewallNetworkRule
-
AzureFirewallDnsProxy
-
-
Select Add diagnostic setting. The Diagnostics settings page provides the settings for the diagnostic logs.
-
In this example, Azure Monitor logs stores the logs, so type Firewall log analytics for the name.
-
Under Log, select AzureFirewallApplicationRule, AzureFirewallNetworkRule, and AzureFirewallDnsProxy to collect the logs.
-
Select the Send to Log Analytics workspace check box , and then pick the Log Analytics workspace to which the logs are to be sent. Here, you should either select the Log Analytics workspace that you created earlier in this procedure, or that Log Analytics workspace that you have used as the destination for all other logs that eG monitors.
-
Finally, to save the configuration, click on the Save button .