AWS Certificate Manager Test
AWS Certificate Manager (ACM) handles the complexity of creating and managing SSL/TLS certificates for your AWS based websites and applications. You can use certificates provided by ACM (ACM Certificates) or certificates that you import into ACM. ACM Certificates can secure multiple domain names and multiple names within a domain. You can also use ACM to create wildcard SSL certificates that can protect an unlimited number of subdomains.
If you are unable to access any web site/web application on the AWS cloud, you may want to check if the certificate attached to that web site/web application has expired, failed, or revoked. This check is made possible by the AWS Certificate Manager test!
This test automatically discovers the certificates managed by the AWS Certificate Manager and reports the current status of each certificate. This way, expired, revoked, failed, and inactive certificates can be identified. Besides expired certificates, the test also leads you to certificates nearing expiry by reporting the number of days each certificate will remain valid. You can also use the detailed diagnostics of this test to know who issued such a certificate, when it was issued, the resources used by that certificate, and the domains included in it.
Target of the test: Amazon Cloud
Agent deploying the test : A remote agent
Outputs of the test : One set of results for certificate managed by the ACM.
First-level descriptor: AWS Region
Second-level descriptor: Certificate Name / ID
| Parameter | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Access Type |
eG Enterprise monitors the AWS cloud using AWS API. By default, the eG agent accesses the AWS API using a valid AWS account ID, which is assigned a special role that is specifically created for monitoring purposes. Accordingly, the Access Type parameter is set to Role by default. Furthermore, to enable the eG agent to use this default access approach, you will have to configure the eG tests with a valid AWS Account ID to Monitor and the special AWS Role Name you created for monitoring purposes.
Some AWS cloud environments however, may not support the role-based approach Note that the Secret option may not be ideal when monitoring high-security cloud environments. This is because, such environments may issue a security mandate, which would require administrators to change the Access Key and Secret Key, often. Because of the dynamicity of the key-based approach, Amazon recommends the Role-based approach for accessing the AWS API. |
|
AWS Account ID to Monitor |
This parameter appears only when the Access Type parameter is set to Role. Specify the AWS Account ID that the eG agent should use for connecting and making requests to the AWS API. To determine your AWS Account ID, follow the steps below:
|
|
AWS Role Name |
This parameter appears when the Access Type parameter is set to Role. Specify the name of the role that you have specifically created on the AWS cloud for monitoring purposes. The eG agent uses this role and the configured Account ID to connect to the AWS Cloud and pull the required metrics. To know how to create such a role, refer to Creating a New Role. |
|
Report for Inuse Certs only |
By default, this flag is set to Yes indicating that this test will report measures only for the certificates that are currently in use. However, if you want this test to report metrics for all the certificates (whether they are in use or not in use) used in the environment, set this flag to No. |
|
AWS Access Key, AWS Secret Key, Confirm AWS Access Key, Confirm AWS Secret Key |
These parameters appear only when the Access Type parameter is set to Secret.To monitor an Amazon cloud instance using the Secret approach, the eG agent has to be configured with the access key and secret key of a user with a valid AWS account. For this purpose, we recommend that you create a special user on the AWS cloud, obtain the access and secret keys of this user, and configure this test with these keys. The procedure for this has been detailed in the Obtaining an Access key and Secret key topic. Make sure you reconfirm the access and secret keys you provide here by retyping it in the corresponding Confirm text boxes. |
|
Proxy Host and Proxy Port |
In some environments, all communication with the AWS cloud and its regions could be routed through a proxy server. In such environments, you should make sure that the eG agent connects to the cloud via the proxy server and collects metrics. To enable metrics collection via a proxy, specify the IP address of the proxy server and the port at which the server listens against the Proxy Host and Proxy Port parameters. By default, these parameters are set to none , indicating that the eG agent is not configured to communicate via a proxy, by default. |
|
Proxy User Name, Proxy Password, and Confirm Password |
If the proxy server requires authentication, then, specify a valid proxy user name and password in the Proxy User Name and Proxy Password parameters, respectively. Then, confirm the password by retyping it in the Confirm Password text box. By default, these parameters are set to none, indicating that the proxy sever does not require authentication by default. |
|
Proxy Domain and Proxy Workstation |
If a Windows NTLM proxy is to be configured for use, then additionally, you will have to configure the Windows domain name and the Windows workstation name required for the same against the Proxy Domain and Proxy Workstation parameters. If the environment does not support a Windows NTLM proxy, set these parameters to none. |
|
Exclude Region |
Here, you can provide a comma-separated list of region names or patterns of region names that you do not want to monitor. For instance, to exclude regions with names that contain 'east' and 'west' from monitoring, your specification should be: *east*,*west* |
|
Default Connection Region |
By default, this test connects to the endpoint URL of the us-east-1 region to collect the required metrics. If the default us-east-1 region is not enabled in the target environment, then, for this test to collect the required metrics, specify the region that is enabled in the target environment. |
|
DD Frequency |
Refers to the frequency with which detailed diagnosis measures are to be generated for this test. The default is 1:1. This indicates that, by default, detailed measures will be generated every time this test runs, and also every time the test detects a problem. You can modify this frequency, if you so desire. Also, if you intend to disable the detailed diagnosis capability for this test, you can do so by specifying none against DD frequency. |
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
|
Measurement |
Description |
Measurement Unit |
Interpretation |
||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Status |
Indicates the current status of this certificate. |
|
The values that this measure can report and their corresponding numeric values are listed in the table below:
If the status of a certificate is abnormal, then you can use the detailed diagnosis of this measure to know who issued an expired, when, which resources are managed by that certificate, and which domains are included in it. You can also use the detailed diagnosis to track the expiry of an issued certificate. Note: Typically, this measure will report the Measure Values listed in the table above to indicate the status of a certificate. In the graph of this measure however, the same will be indicated using the numeric equivalents only. |
||||||||||||||||
|
Certificate validity |
Indicates the number of days by which this certificate will expire. |
Days |
A very low value for this measure indicates that the certificate is set to expire shortly. If If this measure reports the value 0, it implies that the certificate has already expired. You can then use the detailed diagnosis of the Status measure of this test to know who issued that certificate, when, and what is the certificate type (whether imported or not) If the certificate that is about to expire is an imported certificate, then ACM will not manage the renewal process of that certificate. In this case, you will have to import a new third-party certificate to replace the expiring one. On the other hand, if the certificate that is about to expire was provided by ACM, then ACM will try to automatically renew that certificate before expiry. |
||||||||||||||||
|
In use |
Indicates whether/not this certificate is in use. |
|
The values that this measure reports and their corresponding numeric values are detailed in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate whether/not a certificate is in use. In the graph of this measure however, the same is indicated using the numeric equivalents. |
The detailed diagnosis of the Status measure reports the certification authority who issued the certificate, the issue date, the certificate type (whether imported or not), the expiry date, the domains included in the certificate, and the resources managed by it. With the help of this information, you can quickly figure out if a certificate is about to expire soon. If this is an imported certificate, then ACM will not manage the renewal process of that certificate. In this case, you will have to import a new third-party certificate to replace the expiring one. On the other hand, if the certificate that is about to expire was provided by ACM, then ACM will try to automatically renew that certificate before expiry.
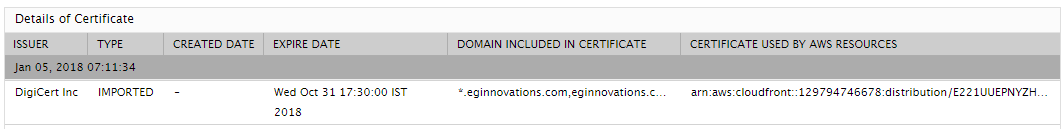
Figure 2 : The detailed diagnosis of the Status measure