AWS Virtual Private Cloud Test
With Amazon Virtual Private Cloud (Amazon VPC), you can launch AWS resources in a logically isolated virtual network that you have defined. This virtual network closely resembles a traditional network that you would operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
Figure 1 depicts a sample VPC and the components that drive that VPC, such as subnets, internet gateways etc.
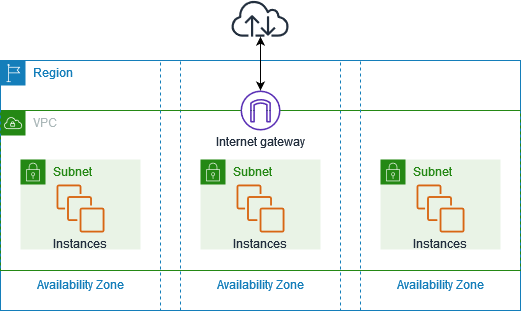
Figure 1 : A sample VPC
This test monitors the VPCs configured in the target AWS account and reports their overall configuration and constitution.
Target of the test: Amazon Cloud
Agent deploying the test: A remote agent
Output of the test: One set of results for the target AWS account
| Parameter | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Access Type |
eG Enterprise monitors the AWS cloud using AWS API. By default, the eG agent accesses the AWS API using a valid AWS account ID, which is assigned a special role that is specifically created for monitoring purposes. Accordingly, the Access Type parameter is set to Role by default. Furthermore, to enable the eG agent to use this default access approach, you will have to configure the eG tests with a valid AWS Account ID to Monitor and the special AWS Role Name you created for monitoring purposes.
Some AWS cloud environments however, may not support the role-based approach Note that the Secret option may not be ideal when monitoring high-security cloud environments. This is because, such environments may issue a security mandate, which would require administrators to change the Access Key and Secret Key, often. Because of the dynamicity of the key-based approach, Amazon recommends the Role-based approach for accessing the AWS API. |
|
AWS Account ID to Monitor |
This parameter appears only when the Access Type parameter is set to Role. Specify the AWS Account ID that the eG agent should use for connecting and making requests to the AWS API. To determine your AWS Account ID, follow the steps below:
|
|
AWS Role Name |
This parameter appears when the Access Type parameter is set to Role. Specify the name of the role that you have specifically created on the AWS cloud for monitoring purposes. The eG agent uses this role and the configured Account ID to connect to the AWS Cloud and pull the required metrics. To know how to create such a role, refer to Creating a New Role. |
|
AWS Access Key, AWS Secret Key, Confirm AWS Access Key, Confirm AWS Secret Key |
These parameters appear only when the Access Type parameter is set to Secret.To monitor an Amazon instance, the eG agent has to be configured with the access key and secret key of a user with a valid AWS account. For this purpose, we recommend that you create a special user on the AWS cloud, obtain the access and secret keys of this user, and configure this test with these keys. The procedure for this has been detailed in the Obtaining an Access key and Secret key topic. Make sure you reconfirm the access and secret keys you provide here by retyping it in the corresponding Confirm text boxes. |
|
Proxy Host and Proxy Port |
In some environments, all communication with the AWS cloud and its regions could be routed through a proxy server. In such environments, you should make sure that the eG agent connects to the cloud via the proxy server and collects metrics. To enable metrics collection via a proxy, specify the IP address of the proxy server and the port at which the server listens against the Proxy Host and Proxy Port parameters. By default, these parameters are set to none , indicating that the eG agent is not configured to communicate via a proxy, by default. |
|
Proxy User Name, Proxy Password, and Confirm Password |
If the proxy server requires authentication, then, specify a valid proxy user name and password in the proxy user name and proxy password parameters, respectively. Then, confirm the password by retyping it in the CONFIRM PASSWORD text box. By default, these parameters are set to none, indicating that the proxy sever does not require authentication by default. |
|
Proxy Domain and Proxy Workstation |
If a Windows NTLM proxy is to be configured for use, then additionally, you will have to configure the Windows domain name and the Windows workstation name required for the same against the proxy domain and proxy workstation parameters. If the environment does not support a Windows NTLM proxy, set these parameters to none. |
|
Exclude Region |
Here, you can provide a comma-separated list of region names or patterns of region names that you do not want to monitor. For instance, to exclude regions with names that contain 'east' and 'west' from |
|
Default Connection Region |
By default, this test connects to the endpoint URL of the us-east-1 region to collect the required metrics. If the default us-east-1 region is not enabled in the target environment, then, for this test to collect the required metrics, specify the region that is enabled in the target environment. |
|
DD Frequency |
Refers to the frequency with which detailed diagnosis measures are to be generated for this test. The default is 1:1. This indicates that, by default, detailed measures will be generated every time this test runs, and also every time the test detects a problem. You can modify this frequency, if you so desire. Also, if you intend to disable the detailed diagnosis capability for this test, you can do so by specifying none against DD frequency. |
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
|
Measurement |
Description |
Measurement Unit |
Interpretation |
|---|---|---|---|
|
VPCs |
Indicates the number of VPCs configured in the target AWS account. |
Number |
Use the detailed diagnosis of this test to view the complete details of each VPC. |
|
Subnets |
Indicates the number of subnets configured across all VPCs in the target AWS account. |
Number |
A subnet is a range of IP addresses in your VPC. A subnet must reside in a single Availability Zone. After you add subnets, you can deploy AWS resources in your VPC. To know what are the subnets that have been configured across VPCs and understand the configuration of each subnet, use the detailed diagnosis of this measure. |
|
Route tables |
Indicates the number of route tables that have been configured. |
Number |
A route table contains a set of rules, called routes, that determine where network traffic from your subnet or gateway is directed. To know what are the route tables that have been configured for each subnet in every VPC, use the detailed diagnosis of this measure. |
|
Internet gateways |
Indicates the number of internet gateways that have been configured for all VPCs in the target AWS account. |
Number |
An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between your VPC and the internet. You can use the detailed diagnosis of this measure to determine the current state of every internet gateway that connects each VPC (in the target AWS account) to the internet. |
|
Egress only internet gateways |
Indicates the number of egress-only internet gateways that have been configured. |
Number |
An egress-only internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows outbound communication over IPv6 from instances in your VPC to the internet, and prevents the internet from initiating an IPv6 connection with your instances. To view more details about these egress-only internet gateways, use the detailed diagnosis of this measure. |
|
DHCP options sets |
Indicates the number of DHCP option sets configured for the VPCs in the target AWS account. |
Number |
Network devices in your VPC use Dynamic Host Configuration Protocol (DHCP). You can use DHCP option sets to control the following aspects of the network configuration in your virtual network: The DNS servers, domain names, or Network Time Protocol (NTP) servers used by the devices in your VPC. Whether DNS resolution is enabled in your VPC. To know what DHCP options have been set per set ID, use the detailed diagnosis of this measure. |
|
Elastic IPs |
Indicates the number of elastic IP addresses assigned to EC2 instances or network interfaces in the VPCs of the target AWS account. |
Number |
An Elastic IP address is a static, public IPv4 address designed for dynamic cloud computing. You can associate an Elastic IP address with any instance or network interface in any VPC in your account. With an Elastic IP address, you can mask the failure of an instance by rapidly remapping the address to another instance in your VPC. To know which elastic IPs have been allocated to which EC2 instances, use the detailed diagnosis of this measure. |
|
Endpoints |
Indicates the number of VPC endpoints that have been configured in the target AWS account. |
Number |
VPC endpoints are virtual devices. They are horizontally scaled, redundant, and highly available Amazon VPC components that allow communication between instances in an Amazon VPC and services without imposing availability risks or bandwidth constraints on network traffic. There are two types of VPC endpoints:
Interface endpoints enable connectivity to services over AWS PrivateLink. A gateway endpoint targets specific IP routes in an Amazon VPC route table, in the form of a prefix-list, used for traffic destined to Amazon DynamoDB or Amazon Simple Storage Service (Amazon S3). Gateway endpoints do not enable AWS PrivateLink. To know what type of endpoints have been configured and for which VPCs, use the detailed diagnosis of this measure. |
|
Endpoint services |
Indicates the number of endpoint services to which VPC endpoints enable connectivity. |
Number |
Endpoint services are services hosted by other AWS customers and partners in their own Amazon VPCs. To know the current status of these endpoint services and the availability zone in which they operate, use the detailed diagnosis of this measure. |
|
NAT gateways |
Indicates the number of NAT gateways are used to connect to services outside the VPCs in this target AWS account. |
Number |
A NAT gateway is a Network Address Translation (NAT) service. You can use a NAT gateway so that instances in a private subnet can connect to services outside your VPC but external services cannot initiate a connection with those instances.
To determine the status of each NAT gateway and to know which NAT gateway is assigned which elastic and private IP address, use the detailed diagnosis of this measuer. |
|
Peering connections |
Indicates the number of VPC peering connections that have been created. |
Number |
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account. The VPCs can be in different Regions (also known as an inter-Region VPC peering connection). Use the detailed diagnosis of this measure to determine which peering connection connects which two VPCs. |
|
Network ACLs |
Indicates the number of network access control lists that have been configured. |
Number |
A network access control list (ACL) allows or denies specific inbound or outbound traffic at the subnet level. You can use the default network ACL for your VPC, or you can create a custom network ACL for your VPC with rules that are similar to the rules for your security groups in order to add an additional layer of security to your VPC. To know which ACL is configured for which subnet, use the detailed diagnosis of this measure. |
|
Security groups |
Indicates the number of security groups created for VPCs in the target AWS account. |
Number |
A security group controls the traffic that is allowed to reach and leave the resources that it is associated with. For example, after you associate a security group with an EC2 instance, it controls the inbound and outbound traffic for the instance. When you create a VPC, it comes with a default security group. You can create additional security groups for a VPC, each with their own inbound and outbound rules. You can specify the source, port range, and protocol for each inbound rule. You can specify the destination, port range, and protocol for each outbound rule. Use the detailed diagnosis of this measure to know which security group is used by which VPC. |
|
Customer gateways |
Indicates the number of customer gateways created to enable VPCs in the target AWS account to communicate with the on-premises network. |
Number |
A customer gateway is a resource that you create in AWS that represents the customer gateway device in your on-premises network. A customer gateway device is a physical device or software application on your side of the Site-to-Site VPN connection. You configure the device to work with the Site-to-Site VPN connection. To know the state of each customer gateway and the VPC connection type that it handles, use the detailed diagnosis of this measure. |
|
Virtual private gateways |
Indicates the number of virtual private gateways that have been created in the target AWS account to enable remote access to the on-premises network. |
Number |
A virtual private gateway is the VPN concentrator on the Amazon side of the Site-to-Site VPN connection. You create a virtual private gateway and attach it to a virtual private cloud (VPC) with resources that must access the Site-to-Site VPN connection. To know which virtual private gateway is configured for which VPC and to determine the current state of each such gateway, use the detailed diagnosis of this measure. |
|
Site to site VPN connections |
Indicates the number of Site-to-site VPN connections that have been configured. |
Number |
By default, instances that you launch into an Amazon VPC can't communicate with your own (remote) network. You can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection, and configuring routing to pass traffic through the connection. To know the details of these VPN connections, use the detailed diagnosis of this measure. |