Automatically Enabling Certificate-based Authentication for an Office 365 Tenant
eG provides a powershell script, which completely automates the process of enabling certificate-based authentication. To run this script and enable cert-based authentication, do the following:
-
Login to the system hosting the eG agent.
-
Open the Windows PowerShell ISE as 'administrator', and run the O365EnableCertBasedAuthentication.ps1 script in the <EG_AGENT_INSTALL_DIR>\lib directory (by clicking on the button indicated by Figure 128).
-
Figure 129 will then appear. In the Username and Password text boxes, specify the credentials of a user with Global administrator rights to the tenant for which certificate-based authentication is to be enabled. If the script should communicate with the tenant via a proxy server, then provide the IP/host name and port number of the Proxy server that the eG agent should use in the Host IP and Port text boxes, respectively. If the Proxy server requires authentication, then specify the credentials of a valid Proxy user against the Username and Password text boxes in the Proxy Details section. Also, in the PFX File Password text box, provide the password using which you want to protect the PFX certificate file that will be created by the script.
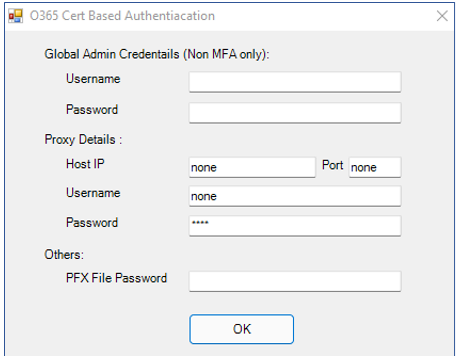
Figure 129 : Configuring the eG agent to communicate with the tenant for enabling cert-based authentication
-
Upon providing valid details in Figure 129, the script automatically performs the following tasks:
-
Connects to the O365 tenant using the Global Admin credentials provided in Figure 129, and creates a new application on Azure AD for the purpose of enabling certificate-based authentication.
-
Creates a self-signed X.509 certificate. The resultant certificate files will be in the .cer and .PFX form.
-
Uploads the .cer certificate file to the Office 365 cloud for secure communication.
-
Grants the Exchange.ManageAsApp permission to the new application in the Office 365 Exchange Online API.
-
Assigns the Exchange Administrator role to the new application
-
Creates an AppInfo folder in the <EG_AGENT_INSTALL_DIR>\agent\O365 diirectory, and copies the certificate files (both the .cer and .PFX files) to this folder.
-
Creates the AppDetails.dat and AppKey.dat files under the AppInfo folder. The tenant ID, ID and secret key of the new application, and certificate thumbprint are automatically saved to these two .dat files.
-
-
Next, proceed to install the PFX certificate on the agent host. For that, navigate to the <EG_AGENT_INSTALL_DIR>\agent\O365\AppInfo directory on the agent host (using Windows Explorer), right-click on the PFX file therein, and select Install PFX. Figure 130 will then appear.
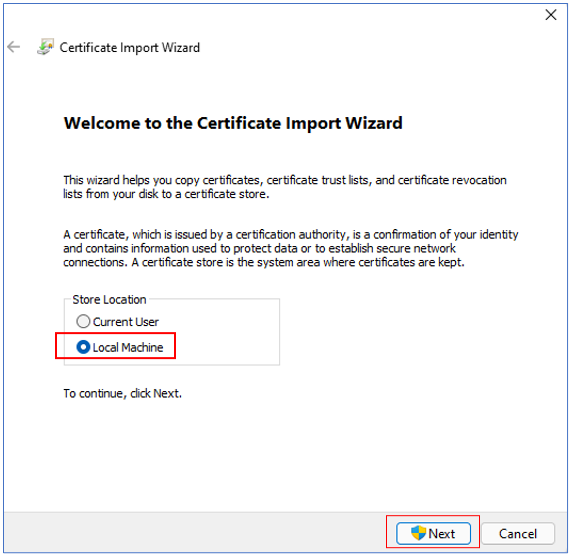
Figure 130 : Selecting Local Machine as Store Location in the Certificate Import Wizard
-
Set Local Machine as the Store Location in Figure 130 and click the Next button.
-
This will invoke Figure 131. Click on Yes here to proceed..
Figure 131 : A message seeking your confirmation to proceed with the installation
-
In Figure 132 that then appears, the path to the PFX file to be installed will by default be displayed in the File name text box. Verify the location of the file, and if it is correct, click on the Next button to proceed.
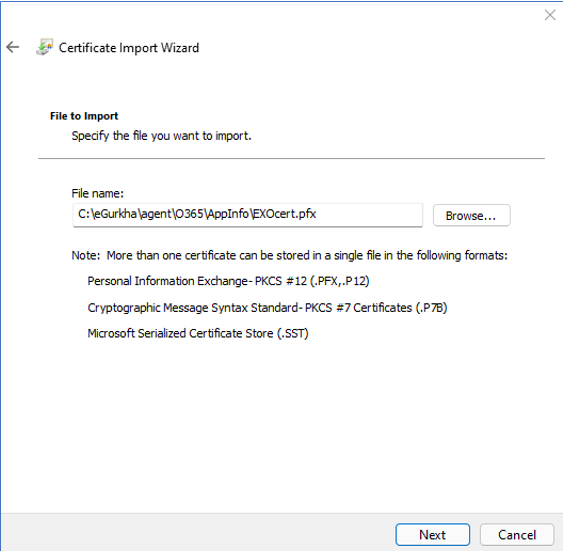
-
Figure 133 will then appear. In the Password text box of Figure 133, enter the same PFX File Password you specified in Figure 129 above. Then, click the Next button.
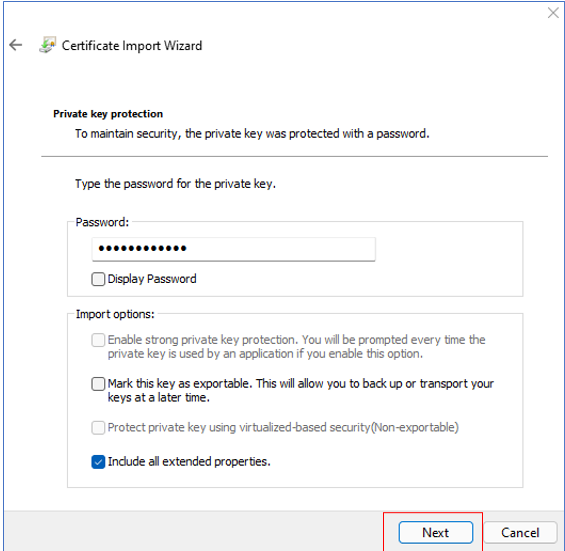
-
Figure 134 will then appear. Here, you need to indicate where the certificate needs to be stored. Select the Automatically select the certificate store based on the type of certificate option in Figure 134. If this option is chosen, then Windows will automatically select a certificate store where the certificate will be stored. Then, click the Next button to move on.
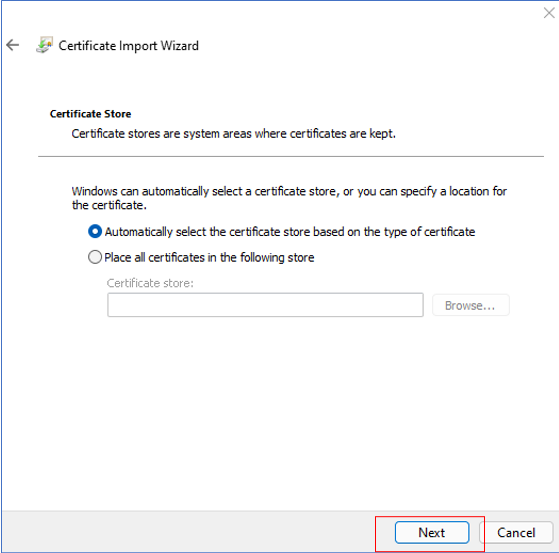
Figure 134 : Allowing Windows to select the certificate store
-
When Figure 135 appears, click the Finish button here to end the installation.
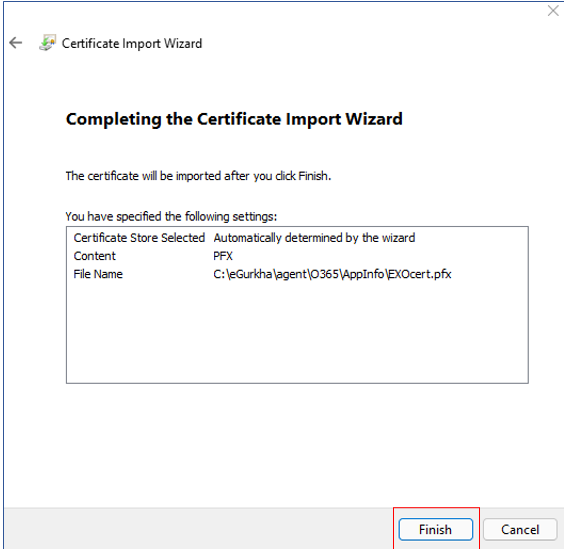
-
If the certificate is successfully imported to the agent host, a message to that effect will appear. Click the OK button here to exit the wizard.
Figure 136 : A message indicating the certificate import is successful
Note:
To make sure that every eG agent that monitors an O365 component uses certificate-based authentication, copy the AppInfo folder that gets automatically created at step 4 to the <EG_AGENT_INSTALL_DIR>\agent\O365 diirectory of every such agent.