This blog post is part 2 of our Monitoring Microsoft Azure Active Directory series. See How to monitor Azure Active Directory for more articles on monitoring Azure AD.
Managing Identity is a big challenge in a cloud environment, especially when users can potentially log in from anywhere. Additionally, users can often use different types of devices to log in and access cloud-hosted resources. Without a central Authentication and Authorization source, it is very difficult to manage who can login to what and who can do what with a cloud resource. On top of that, there can be thousands of identical identities from different organizations trying to consume the cloud resources. Microsoft solves all the above challenges with the help of Azure Active Directory (Azure AD).
We can get a decent basic understanding of Azure Active Directory from the Microsoft documentation, and I’ve written a quick overview Azure Active Directory (Azure AD) – 101, which includes the relationship between Active Directory and Azure AD Connector.
Azure AD as the name suggests is a directory of all your usernames, credentials, and access rights to resources. It is designed to operate in a cloud infrastructure using REST APIs to pass data from one application and system to the other. Azure AD is based upon the building blocks of users and groups.
Importance of Monitoring Users Created in Azure Active Directory
In this blog post, I’ll focus on monitoring users within Azure AD, including a list of key checks and questions you should consider when evaluating your auditing, security, and visibility needs for managing users.
The user account in Azure AD is like a user account in Active Directory. An Azure AD can have user accounts from :
- Cloud identities
- Synced identities
Cloud identities are accounts that exist only in Azure AD whereas synced identities are those that exist in an on-premises Active Directory and are being synchronized to Azure AD using a directory sync tool called “Azure AD Connect”.
Microsoft has recently enabled organizations using the Azure Virtual Desktop (AVD) virtual desktop infrastructure (VDI) service to support the so-called “cloud-only users.”
Azure AD is now the core mechanism through which enterprises can manage different applications, devices, and users across several tenants. Organizations use Azure AD for controlling identity and access management, allowing sign-in to multiple Microsoft applications and hundreds of SaaS applications seamlessly, protecting users from malicious threat actors and importantly allowing collaboration between external guests and Azure AD users.
There are several methods to add users to your Azure AD:
- Most organizations that already use On-Premises Active Directory can use Azure AD Connect to sync their users and groups to Azure AD.
- You can manually create the users in Azure AD management portal.
- Users can be added by running AAD cmdlets.
- Users can be added via the Azure AD Graph API.
With Microsoft recently announcing general availability for Azure Virtual Desktop (AVD) with the VMs joined to Azure AD rather than Active Directory, there will be a trend for some users to move to Azure AD where possible.
So, user accounts in Azure AD can grow quickly based on the business/organizational requirements. As Azure AD resides on the cloud, tenants are vulnerable to ransomware attacks, password spraying, brute force attacks, etc. Examples of recent Azure AD attacks and known security concerns, include:
- How Azure AD Could Be Vulnerable to Brute-Force and DOS Attacks
- New Azure Active Directory password brute-forcing flaw has no fix
Key questions that administrators of Azure Active Directory need answers to:
Ideally, an Azure administrator will need to find out (and better still, proactively monitor) the following from the Azure AD:
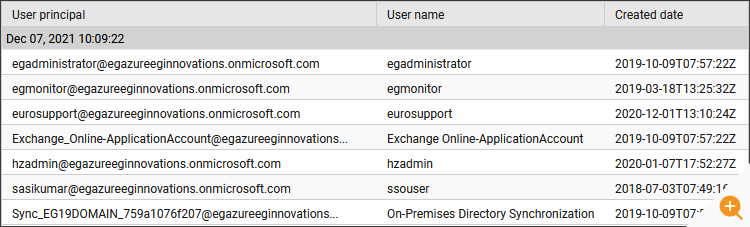
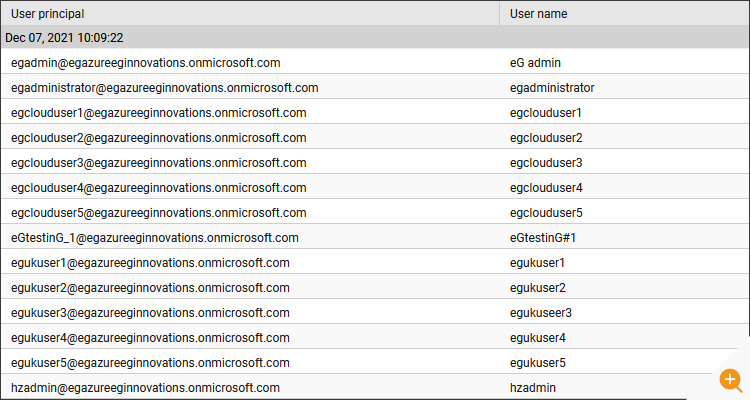
- How many users have been created in Azure AD?
- How many users are synced from On-Premises Active Directory and where were they synced and when did the last synchronization happen?
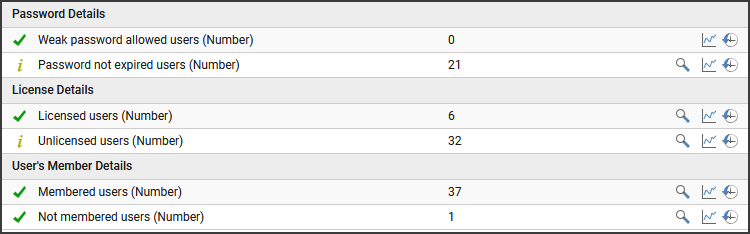
- How many users have weak passwords?
- How many users have a password with “is set not to expire” status?
- Are there any unlicensed users in the Azure tenant?
- Are there any disabled accounts in the Azure tenant?
- Are there any user accounts that are not part of any of the Azure AD Groups?
- Are there any stale user accounts in the Azure tenant?
- Have there been any malicious sign-in attempts?
- Have any risky sign-ins happened recently?
- Are any App registrations going to expire either in client secrets or SSL certificates?
- What are the roles and permissions of App registrations?
- Have any brute force attacks happened recently for the tenant?
What is available for tracking users in Azure Active Directory today?
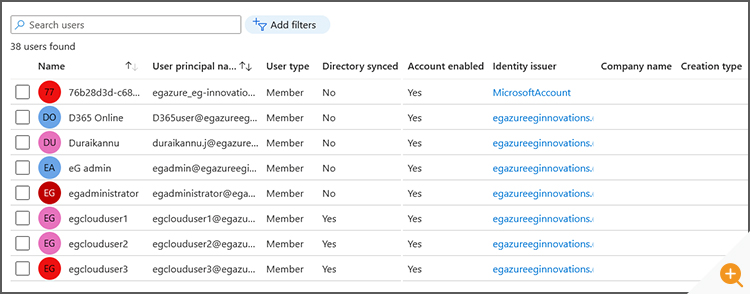
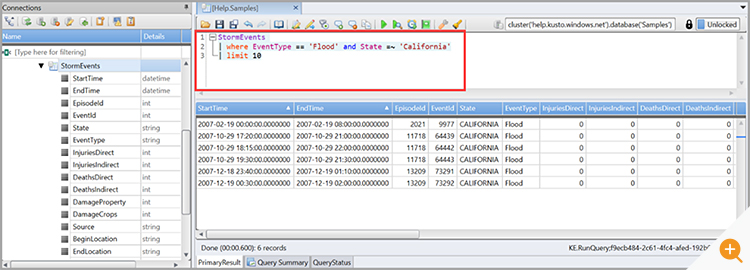
Microsoft Azure Active Directory provides a flat overview screen (see Figure 2 below). This is a grid-like view that rapidly becomes unwieldy as the number of users increases beyond a handful.
To identity misuse and breaches, Azure AD administrators have to use the native Azure Monitor, augment it with custom Kusto Queries (KQL), and then rely on Log Analytics Workspaces and workbooks available via GitHub repository for detection and analysis.
Azure expert Marius Sandbu’s recent tutorial “Auditing and Security Monitoring of Azure Active Directory” includes details on getting started with Kusto.
The whole process of analyzing Azure metrics and writing custom KQL queries is time-consuming and needs expertise in terms of what you are looking for and where.
What is a Kusto Query?
Azure Data Explorer aka Kusto is a log analytics cloud platform optimized for ad-hoc big data queries.
A Kusto query is a read-only request to process data and return results. The request is stated in plain text, using a data-flow model designed to make the syntax easy to read, author, and automate. The query uses schema entities that are organized in a hierarchy similar to SQL’s: databases, tables, and columns.
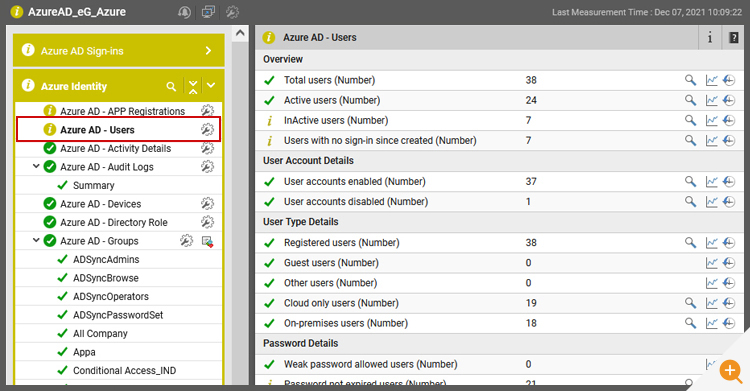
Monitoring Azure Active Directory Users with eG Enterprise
eG Enterprise’s Azure Active Directory monitoring answers all the common questions about Azure AD users out of the box without having to write any KQL queries. Dashboards can be accessed out of the box or created with just a few clicks without having to rely on public domain workbooks.
Besides continually monitoring logs, metrics, and error messages, eG Enterprise also automatically performs deeper diagnostic tests, if issues exist. For example, if inactive users are detected or failed logins occur, details on those users or reasons for failure are collected and analyzed.
Coupled with automated static and dynamic thresholds, anomalies, and unusual events automatically trigger notifications that pinpoint the underlying root cause of the problem.
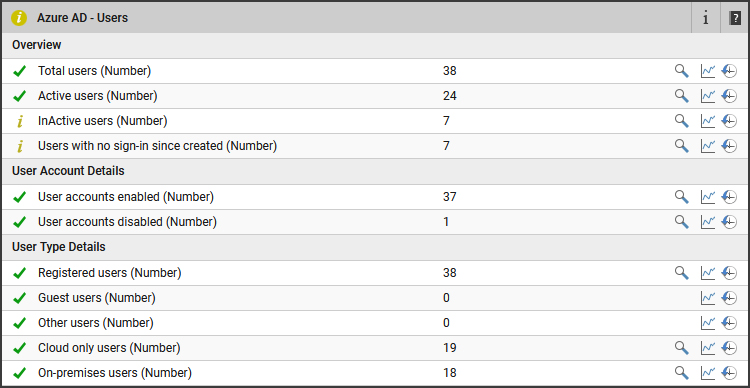
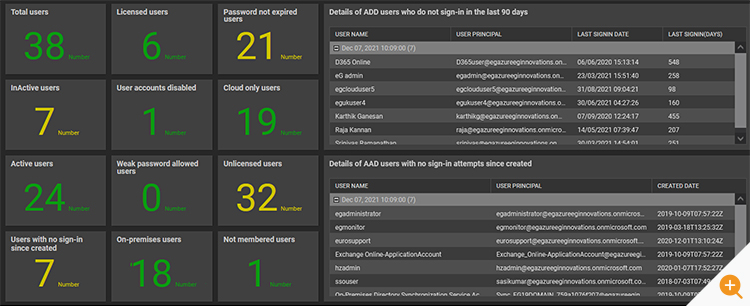
The detailed diagnosis provided enables an Azure AD administrator to instantly access additional details, for example:
-
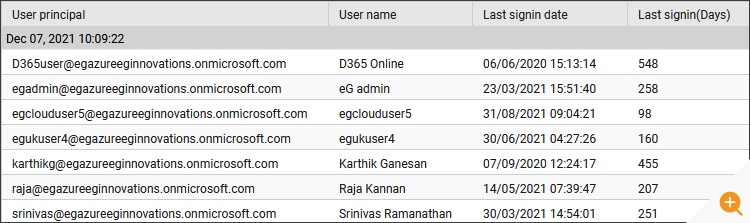
- Details of stale users (Users, who are not signed-in in the last 90 days)
-
- Details of users, who are not signed-in after they are created in Azure AD
-
- Details of users whose passwords do not expire (subject to attacks, if exposed)
Beyond the real-time monitoring component, the core eG Enterprise product allows data which is collected to be accessed via:
- Fully customizable dashboards, popular for frontline helpdesk usage that can be published on role-based identities and in kiosk (“TV Mode”) to large screens – see How to Add a Custom Dashboard (eginnovations.com)
- Fully featured administrator apps for Android and iOS – see IT Remote Monitoring Software
- Full API integrations with SMS/Email alerting and service/helpdesk tools, such ServiceNOW, Jira, Slack, Autotask, and more. Ensure incidents with Azure AD are fully managed by process, see Service and Help Desk Automation Strategies | eG Innovations.
- Historical reporting and insights analysis for management visibility and forecasting/capacity planning – see The eG Reporter (eginnovations.com)
- AIOps capabilities using Machine Learning technologies learn what is normal user behavior for organizations and provide alerting of anomalous behavior that may be indicative of malicious access attempts, learn more.
In my next blog post, I intend to cover how eG Enterprise can help in finding malicious sign-in attempts and brute force attacks via our comprehensive monitoring for Azure Audit logs and Sign-In logs.
Many of our customers use eG Enterprise to monitor other components and their Azure infrastructure and beyond to other clouds and on-premises infrastructure and applications, please see links for information on monitoring:
eG Enterprise is an Observability solution for Modern IT. Monitor digital workspaces,
web applications, SaaS services, cloud and containers from a single pane of glass.





 Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way.
Babu is Head of Product Engineering at eG Innovations, having joined the company back in 2001 as one of our first software developers following undergraduate and masters degrees in Computer Science, he knows the product inside and out. Based within our Singapore R&D Management team, Babu has undertaken various roles in engineering and product management becoming a certified PMP along the way. 


