NPS Authentication Proxy Test
Network Policy Server (NPS) can be used as a RADIUS proxy to provide the routing of RADIUS messages between RADIUS clients access servers and RADIUS servers that perform user authentication, authorization, and accounting for the connection attempt. When used as a RADIUS proxy, NPS is a central switching or routing point through which RADIUS access and accounting messages flow.
The below shows NPS as a RADIUS proxy between RADIUS clients (access servers) and either RADIUS servers or another RADIUS proxy.
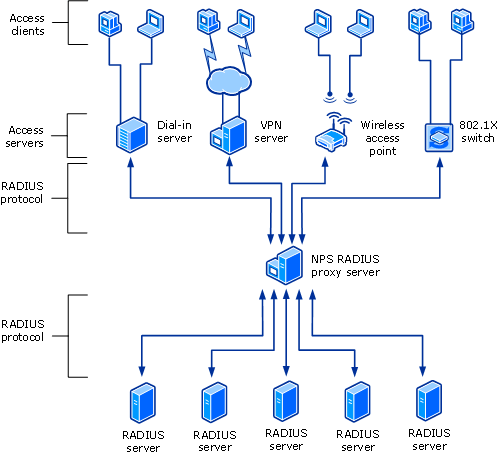
Figure 1 : How NPS RADIUS Proxy works
When NPS is used as a RADIUS proxy between a RADIUS client and a RADIUS server, RADIUS messages for network access connection attempts are forwarded in the following way:
- Access servers, such as dial-up network access servers, virtual private network (VPN) servers, and wireless access points, receive connection requests from access clients.
- The access server, configured to use RADIUS as the authentication, authorization, and accounting protocol, creates an Access-Request message and sends it to the NPS server that is being used as the NPS RADIUS proxy.
- The NPS RADIUS proxy receives the Access-Request message and, based on the locally configured connection request policies, determines where to forward the Access-Request message.
- The NPS RADIUS proxy forwards the Access-Request message to the appropriate RADIUS server.
- The RADIUS server evaluates the Access-Request message.
- If required, the RADIUS server sends an Access-Challenge message to the NPS RADIUS proxy, where it is forwarded to the access server. The access server processes the challenge with the access client and sends an updated Access-Request to the NPS RADIUS proxy, where it is forwarded to the RADIUS server.
- The RADIUS server authenticates and authorizes the connection attempt.
- If the connection attempt is both authenticated and authorized, the RADIUS server sends an Access-Accept message to the NPS RADIUS proxy, where it is forwarded to the access server.
- If the connection attempt is either not authenticated or not authorized, the RADIUS server sends an Access-Reject message to the NPS RADIUS proxy, where it is forwarded to the access server.
If the RADIUS server challenges or rejects connection requests frequently, the NPS RADIUS Proxy will transmit the same to the access servers. This in turn can cause many clients to be denied connections to access servers; some others may experience significant delays in connecting. Malformed request packets and those with invalid attributes/addresses can also be responsible for authentication delays/denials. Sometimes, a processing bottleneck on the NPS RADIUS Proxy server can also result in a slowdown in authentication. To enable clients to access remote services rapidly, administrators should keep a close watch on how the NPS RADIUS Proxy handles the requests and responses it receives, detect abnormalities rapidly, and quickly initiate measures to resolve them. The NPS Authentication Proxy test helps administrators do just that!
This test keeps tabs on the access requests the NPS RADIUS Proxy receives from access servers and reports the rate at which the RADIUS server challenges / rejects these requests, thereby enabling administrators to instantly spot an abnormal number of challenges and rejections. Additionally, the test also reveals the rate at which erroneous request/response packets are received by the NPS RADIUS Proxy, thus providing administrators with effective pointers to what could be causing the high rate of challenges, rejects, or retransmisssions – is it because of malformed packets? packets with invalid authentication attributes? packets with invalid addresses? or non-RADIUS packets? The test also sheds light on the poor processing ability of the NPS RADIUS Proxy by reporting the number of pending requests on the proxy from time to time.
Target of the test : An NPS server
Agent deploying the test : An internal agent
Outputs of the test : One set of results for the NPS RADIUS Proxy
| Parameters | Description |
|---|---|
|
Test period |
This indicates how often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
Port |
The port at which the NPS server listens. The default is NULL. |
| Measurement | Description | Measurement Unit | Interpretation |
|---|---|---|---|
|
Access-Accepts |
Indicates the rate at which RADIUS Access-Accept packets were received by the proxy. |
Accepts/Sec |
|
|
Access-Challenges |
Indicates the rate at which RADIUS Access-Challenge packets were received by the NPS RADIUS proxy from the RADIUS server. |
Challenges/Sec
|
A low value is desired for this measure. A high value indicates that the RADIUS server challenged many access requests, forcing the access server to send an updated Access-Request to it, through the NPS RADIUS proxy. In such cases, access clients are bound to experience delays in accessing the server. |
|
Access-Rejects |
Indicates the rate at which RADIUS Access-Reject packets were sent by the RADIUS server to the NPS RADIUS Proxy. |
Rejects/Sec |
Ideally, the value of this measure should be 0 or very low. A high value indicates too many or too frequent request rejections, which in turn may cause access clients to be denied access to the server. |
|
Access-Requests |
Indicates the rate at which Access-Request packets were received by the NPS RADIUS Proxy from the access servers. |
Reqs/Sec |
This is a good indicator of the load on NPS.
|
|
Bad authenticators |
Indicates the rate at which NPS RADIUS Proxy received access requests containing an invalid Message Authenticator attribute. |
Reqs/Sec |
Ideally, the value of this measure should be 0. |
|
Packets dropped |
Indicates the rate at which request packets received by the NPS RADIUS proxy were silently discarded for a reason other than "malformed," "invalid Message Authenticator," or "unknown type". |
Packets/Sec |
Ideally, the value of this measure should be 0. |
|
FullAccess-Decisions |
Indicates the rate at which Full-access decisions were received the NPS RADIUS Proxy. |
Decisions/Sec |
The RADIUS server grants an access client full access if the client meets the defined health policies.
|
|
Invalid addresses |
Indicates the rate at which the NPS RADIUS Proxy received packets from unknown addresses. |
Packets/Sec |
Ideally, this value should be 0. |
|
Malformed packets |
Indicates the rate at which the NPS RADIUS Proxy received malformed packets. |
Packets/Sec |
Ideally, the value of this measure should be 0. |
|
Packets received |
Indicates the rate at which packets were received by the NPS RADIUS Proxy. |
Packets/Sec |
|
|
Probation-Decisions |
Indicates the rate at which probation-decisions were received from the NPS RADIUS Proxy. |
Decisions/Sec |
If the RADIUS server grants an access client full access but for a limited period only, the client is said to be on probation. This can happen if the RADIUS server finds that the client did not fulfill certain health policy requirements. |
|
Quarantine-Decisions |
Indicates the rate at which quarantine decisions were sent from the NPS RADIUS Proxy. |
Decisions/Sec |
When a remote access client dials in or connects via VPN to an access server, by default only the user’s credentials (account name and password) are checked to determine whether access is granted. This means a computer that does not meet the network’s policy requirements could still connect to the server and the network from a remote location. When quarantine control is deployed, after the user’s credentials are authenticated the connection is “quarantined.” In quarantine mode, the computer has an IP address and has limited access to some network resources (called quarantine resources) such as a DNS server and perhaps a file server or web serverfrom which it can download files necessary to comply with the policies or where the user can get more information, but cannot access the rest of the network. |
|
Request timeouts |
Indicates the rate at which requests to the NPS RADIUS proxy timed out. |
Reqs/Sec |
A high value indicates frequent timeouts. Under such circumstances, you may want to consider changing the timeout setting for requests, so that timeouts are kept at a minimum. |
|
Retransmissions |
Indicates the rate at which requests were retransmitted to the NPS RADIUS Proxy. |
Reqs/Sec |
Retransmits can increase the number of requests to the proxy, thus overloading it. It is hence good practice to keep the rate of retransmissions minimal. One of the reasons for a high rate of retransmissions is a low Timeout setting on NPS RADIUS Proxy. If the value of this measure is very high, you may want to change the timeout setting to reduce retransmits. |
|
Unknown type |
Indicates the average number of unknown type (non-RADIUS) packets received by this servethe NPS RADIUS proxy per second. |
Packets/Sec |
|
|
Pending requests |
Indicates the rate of requests destined for the proxy that have not yet timed out or received a response. |
Reqs/Sec |
A high value could either indicate a processing bottleneck on the NPS RADIUS Proxy or a high timeout setting. In the case of the latter, you may want to consider modifying the timeout setting to minimize the number of pending requests. In the case of the former, you may want to consider adding more RADIUS servers, so that the NPS RADIUS Proxy is able to dynamically balance the load of connection requests across multiple RADIUS servers and thus speed up processing. |