Azure Firewall Test
Azure Firewall is a cloud-native and intelligent network firewall security service that provides the best of breed threat protection for your cloud workloads running in Azure.
The continued availability and good health of the firewall service is essential to protect the applications running on the Azure cloud from malicious attacks. Also, to keep suspicious traffic away, the administrators should know what traffic to allow and what should be blocked, and accordingly configure firewall rules. The Azure Firewall test helps administrators address both these security requirements!
This test monitors each Azure firewall that is configured for the target subscription and reports the status of that firewall from time-to-time. Administrators are alerted if a firewall slides into a degraded/unhealthy state. Alerts are also sent out if the firewall's ability to differentiate between malicious and non-malicious traffic is compromised. The test also periodically scans the Azure Firewall logs for application, network, and NAT rule hits, and instantly notifies administrators if network traffic matches any of the configured rules. Detailed diagnostics reveal the complete details of the matching rules, so administrators can review the rules for correctness and effectiveness. From the firewall logs, the test also reads information pertaining to which IP addresses were denied access and which were allowed, thereby turning the spotlight on traffic that is 'suspect' and therefore, warrants further investigation. These analytics also help administrators determine whether/not the 'right' traffic was only allowed access. Changes, if required, can be made to firewall rules based on these findings.
Note:
Typically, to consolidate log entries, correlate log data, and perform complex analysis, the Firewall logs are often sent to one/more Log Analytics Workspaces. This test reports valid metrics on firewall rule hits by reading data from these Log Analytics Workspaces only. If the firewall logs are not sent to any Log Analytics Workspace, then this test will only report the value 0 for most of its measures. To avoid this, before configuring this test, make sure that the firewall logs are configured to be sent to at least one Log Analytics Workspace. Follow the steps discussed in Configuring the Activity Log to be Sent to a Log Analytics Workspace to achieve this.
Target of the Test: A Microsoft Azure Subscription
Agent deploying the test: A remote agent
Output of the test: One set of results for each Azure firewall configured for each resource group in the target Azure subscription
| Parameters | Description |
|---|---|
|
Test Period |
How often should the test be executed. |
|
Host |
The host for which the test is to be configured. |
|
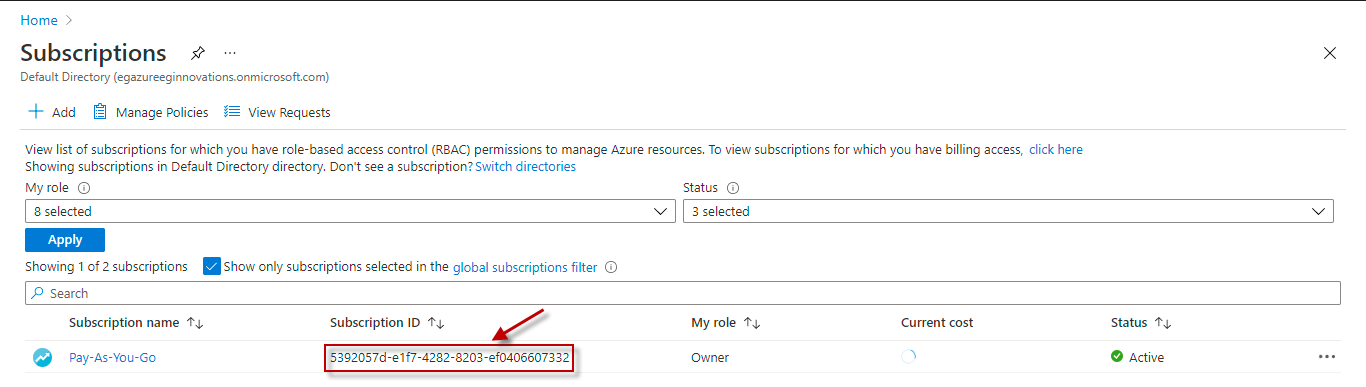
Subscription ID |
This field will be automatically populated if you have chosen to automatically fulfill the pre-requisites for monitoring the Microsoft Azure Subscription. Specify the GUID which uniquely identifies the Microsoft Azure Subscription to be monitored in this text box
|
|
Tenant ID |
This field will be automatically populated if you have chosen to automatically fulfill the pre-requisites for monitoring the Microsoft Azure Subscription. Specify the Directory ID of the Azure Entra ID tenant to which the target subscription belongs in this text box |
|
Client ID, Client Password, and Confirm Password |
To connect to the target subscription, the eG agent requires an Access token in the form of an Application ID and the client secret value. For this purpose, you should register a new application with the Microsoft Entra tenant. To know how to create such an application and determine its Application ID and client secret, refer to Configuring the eG Agent to Monitor a Microsoft Azure Subscription Using Azure ARM REST API. Specify the Application ID of the created Application in the Client ID text box and the client secret value in the Client Password text box |
|
Proxy Host and Proxy Port |
In some environments, all communication with the Azure cloud be routed through a proxy server. In such environments, you should make sure that the eG agent connects to the cloud via the proxy server and collects metrics. To enable metrics collection via a proxy, specify the IP address of the proxy server and the port at which the server listens against the Proxy Host and Proxy Port parameters. By default, these parameters are set to none, indicating that the eG agent is not configured to communicate via a proxy, by default. |
|
Proxy Username, Proxy Password and Confirm Password |
If the proxy server requires authentication, then, specify a valid proxy user name and password in the Proxy Username and Proxy Password parameters, respectively. Then, confirm the password by retyping it in the Confirm Password text box. |
|
Log Analytics Workspace Name |
Typically, to consolidate log entries, correlate log data, and perform complex analysis, Firewall logs are often sent to one/more Log Analytics Workspaces. By default, the Log Analytics Workspace Name parameter is set to All. This indicates that the test reads log data from all Log Analytics Workspaces configured for the target subscription, by default. However, if you want the test to use only those Log Analytics Workspaces to which the Firewall logs are sent, then provide the names of these workspaces here as a comma-separated list. To determine the names of the workspaces, do the following:
|
|
Show Category DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique categories measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits per category as part of the detailed analytics of the Unique categories measure. |
|
Show Operation DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique operations measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits per operation as part of the detailed analytics of the Unique operations measure. |
|
Show Protocol DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique protocols measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits per protocol as part of the detailed analytics of the Unique protocols measure. |
|
Show SourceIP DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique source IPs measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits per source IP address as part of the detailed analytics of the Unique source IPs measure. |
|
Show TargetIP DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique target IPs measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits per destination IP address as part of the detailed analytics of the Unique target IPs measure. |
|
Show AllowedIP DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique allowed target IPs measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits for every target IP to which traffic was allowed, as part of the detailed analytics of the Unique allowed target IPs measure. |
|
Show DeniedIP DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique denied target IPs measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits for every target IP to which traffic was blocked, as part of the detailed analytics of the Unique denied target IPs measure. |
|
Show Action DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique actions measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits for every action (Allow, Deny) taken, as part of the detailed analytics of the Unique actions measure. |
|
Show RuleColl DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique rule collections measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of rule hits for every rule collection configured, as part of the detailed analytics of the Unique rule collections measure. |
|
Show ApplicationRule DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique application rules measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of times each unique application rule found a match, as part of the detailed analytics of the Unique application rules measure. |
|
Show NetworkRule DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique network rules measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of times each unique network rule found a match, as part of the detailed analytics of the Unique network rules measure. |
|
Show Rules DD |
By default, this parameter is set to False. This means that detailed diagnostics will not be available, by default, for the Unique rules measure reported by this test. If you want to enable detailed reporting for this measure, then set this parameter to True. Once this is done, then you will be able to view the number of times each unique rule found a match, as part of the detailed analytics of the Unique rules measure. |
|
Detailed Diagnosis |
To make diagnosis more efficient and accurate, the eG Enterprise embeds an optional detailed diagnostic capability. With this capability, the eG agents can be configured to run detailed, more elaborate tests as and when specific problems are detected. To enable the detailed diagnosis capability of this test for a particular server, choose the On option. To disable the capability, click on the Off option. The option to selectively enable/disable the detailed diagnosis capability will be available only if the following conditions are fulfilled:
|
| Measurement | Description | Measurement Unit | Interpretation | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Provisioning status |
Indicates the current provisioning state of this firewall. |
|
The values reported by this measure and its numeric equivalents are mentioned in the table below:
Note: By default, this measure reports the Measure Values listed in the table above to indicate the provisioning status of a firewall. In the graph of this measure however, the same is represented using the numeric equivalents only. Use the detailed diagnosis of this measure to know the location of the firewall, and the zones and tags associated with it. |
||||||||||
|
Threat intelligence mode |
Indicates whether/not threat intelligence filtering is enabled for this firewall. |
|
Threat intelligence-based filtering can be enabled for your firewall to alert and deny traffic from/to known malicious IP addresses and domains. The values reported by this measure and its numeric equivalents are mentioned in the table below:
In the 'Alert' mode, an alert is logged when a rule is triggered. In the 'Deny' mode, the traffic is denied. Note: By default, this measure reports the Measure Values listed in the table above to indicate the threat intelligence mode set for a firewall. In the graph of this measure however, the same is represented using the numeric equivalents only. |
||||||||||
|
Total IPs configured |
Indicates the number of public IP addresses configured for this firewall. |
Number |
Use the detailed diagnosis of this measure to know the public IP addresses configured, the private IP address that maps to each, the allocation mode, SKU name, tier, version, and how long each IP address has been idle. |
||||||||||
|
Application rules |
Indicates the number of application rules that have been configured for this firewall. |
Number |
With Azure Firewall, you can configure: Application rules that define fully qualified domain names (FQDNs) that can be accessed from a subnet. The detailed diagnosis of this measure, if enabled, provides the complete details of the configured application rules. |
||||||||||
|
Network rules |
Indicates the number of network rules that have been configured for this firewall. |
Number |
Network rules define source address, protocol, destination port, and destination address. The detailed diagnosis of this measure, if enabled, provides the complete details of the configured network rules. |
||||||||||
|
NAT rules |
Indicates the number of NAT rules that have been configured for this firewall. |
Number |
A NAT rule is a routing rule, directing traffic from a public IP address to a private IP address. The detailed diagnosis of this measure, if enabled, provides the complete details of the configured NAT rules. |
||||||||||
|
Firewall health status |
Indicates the current health of this firewall based on SNAT port availability. |
Percent |
If the SNAT port usage is greater than 95%, then the value of this measure will be 50%. This represents a Degraded state. In this state, the firewall keeps processing traffic and existing connections are not affected. However, new connections may not be established intermittently. If SNAT port usage is lesser than 95%, then the value of this measure will be 100%. This means that the firewall is in a Healthy state. If no SNAT ports are used, then the value of this measure will be 0%. |
||||||||||
|
Data processed |
Indicates the total amount of data traversing this firewall. |
MB |
|
||||||||||
|
Throughput |
Indicates the rate at which data was traversing this firewall. |
MB/Sec |
|
||||||||||
|
NAT utilization |
Indicates the percentage of SNAT ports utilized by this firewall. |
Percent |
If the value of this measure is greater than 95%, then the value of the Firewall health status measure will be 50%. This indicates that the firewall is in a Degraded state. If the value of this measure is lesser than 95%, then the value of the Firewall health status measure will be 100%. This indicates that the firewall is in a Healthy state. |
||||||||||
|
Unique categories |
Indicates the total number of rule hits across all unique categories of traffic traversing this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per unique category. |
||||||||||
|
Unique operations |
Indicates the total number of rule hits across all unique operations performed by traffic traversing this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per unique operation. |
||||||||||
|
Unique protocols |
Indicates the total number of rule hits across all unique traffic protocols traversing this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per protocol. |
||||||||||
|
Unique source IPs |
Indicates the total number of rule hits across all unique sources from which this firewall received traffic. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per unique source IP address. |
||||||||||
|
Unique target IPs |
Indicates the total number of rule hits across all unique destinations to which this firewall sent traffic. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per unique target IP address. |
||||||||||
|
Unique allowed target IPs |
Indicates the total number of rule hits across all IP addresses to which traffic was allowed by this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per target IP address to which traffic was allowed. |
||||||||||
|
Unique denied target IPs |
Indicates the total number of rule hits across all IP addresses to which traffic was denied by this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per target IP address to which traffic was denied. |
||||||||||
|
Unique actions |
Indicates the total number of rule hits across all unique actions configured for this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per action. |
||||||||||
|
Unique rule collections |
Indicates the total number of rule hits across all unique rule collections configured for this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per rule collection. |
||||||||||
|
Unique application rules |
Indicates the total number of rule hits across all unique application rules configured for this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per unique application rule |
||||||||||
|
Unique network rules |
Indicates the total number of rule hits across all unique network rules configured for this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per unique network rule. |
||||||||||
|
Unique rules |
Indicates the total number of rule hits across all unique rules configured for this firewall. |
Number |
Use the detailed diagnosis of this measure to know the number of rule hits per unique rule. |