System Overview
In complex IT environments, administrators often need to quickly identify systems that meet specific configuration or deployment requirements. Traditionally, this involves manually checking the configuration details of every server in the environment, an effort that becomes increasingly time-consuming and error-prone as the infrastructure grows. For example, if administrators need to locate Windows servers running a specific OS version, or identify systems based on hardware characteristics or deployment type (such as Virtual or Physical), they would otherwise have to inspect each machine individually to determine which ones satisfy their criteria.
To eliminate this manual overhead and to provide administrators with a unified, accurate, and easily accessible source of system configuration data, the eG Enterprise platform offers the System Overview report. This report consolidates essential configuration details of all agent-based Microsoft Windows components into a single, comprehensive view. By displaying key information, such as component name, type, IP and physical addresses, system model, OS name, and OS version, the System Overview report enables administrators to quickly compare configuration attributes across systems and effortlessly identify the servers that best meet their operational, compliance, or deployment needs.
To view the system-level configuration details of agent-based Microsoft Windows components, do the following:
-
Navigate through Configuration > Consolidated View to access the consolidated configuration page.
-
Select Microsoft Windows as component type from the Component Type list box as depicted in Figure 1
-
This will list all the components of the chosen type in the Components list box. Select one or more components from the list box as required.
-
All the configuration parameters that are supported by the components of the chosen type, will then be displayed in the Report Type drop-down list. Choose System Overview from the Report Type drop-down list.
-
Finally, click the SUBMIT button (see Figure 1).
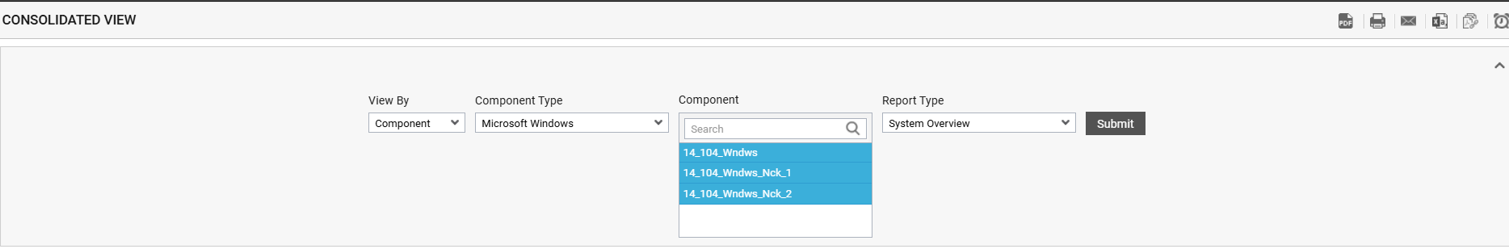
-
This will invoke the System Overview report as in Figure 2, that displays tabular information based on the selected component.
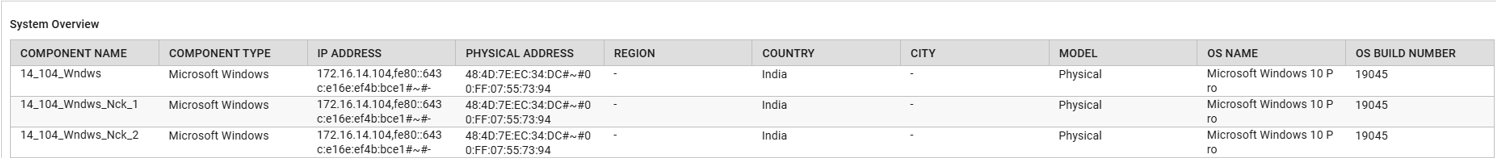
Figure 2 : The System Overview report showing the details of the system configuration.
-
The System Overview report helps administrators understand the following:
-
The Component Name and Component Type columns provides a clear mapping of all Microsoft Windows systems monitored, ensuring full visibility into available infrastructure resources.
-
The IP Address shows the network IP assigned to the system. This helps administrators verify network reachability, troubleshoot connectivity issues, and map each system to the correct subnet or VLAN.
-
The Physical Address displays the MAC address of the network interface. This is useful for identifying the actual hardware or virtual network adapter, validating NIC bindings, and ensuring correct asset tracking.
-
The Model (Virtual Machine / Physical Machine) column indicates whether the system is hosted on physical hardware or runs as a virtual instance. This helps IT teams differentiate workloads for capacity planning, hardware lifecycle management, and virtualization optimization.
-
The Location ( Region, City, and Country) shows the geographical or logical location of the system, such as data center, site, or region, enabling administrators to perform regional analysis, enforce location-based policies, and understand distribution of assets.
-
The OS Name displays the operating system installed on the system (e.g., Windows Server 2016, Windows 10). This helps in identifying OS diversity, ensuring OS consistency, and validating platform compatibility across the environment.
-
The OS Build Number indicates the specific build number of the installed operating system. This is essential for:
-
Identifying whether systems are running the latest patches or cumulative updates,
-
Detecting unsupported or vulnerable builds,
-
Planning targeted update rollouts, and
-
Ensuring compliance with OS lifecycle and security policies.
-
-